TL;DR
After the Bank of Spain (BDE) published the TIBER-ES guide adapted to the national territory in January 2022, I was thinking about the complexity that in some cases it would entail for Threat Intelligence and Red Team providers to give this service to financial entities.
For this reason, I wanted to carry out a development so that the Threat Intelligence teams speed up their work through predefined cases of the famous platform used in the world of CTI called The Hive.
The developed cases contemplate all the phases that TIBER-EU mentions in its documentation, in addition I have also included good practices and ways of facing some phases.
The fact of using The Hive is due to the following reasons:
- Allows to merge cases
- Can be integrated with MISP
- Can be integrated with Cortex and its analyzers
- Case templates can be created
GitHub project: https://github.com/jstnk9/TIBER-Cases
Abbreviations
| Key | Description |
|---|---|
| Entity | The term Entity during this blog and The Hive cases, refers to the entity that is going to carry out the TIBER-EU exercises. |
| TI | Threat Intelligence Provider. Is the provider of threat intelligence services for the Entity. |
| RT | Red Team Provider. Is the provider of red teaming services for the Entity. |
| WT | White Team. Team responsible of the scope and operative execution of the exercises. |
| BT | Blue Team. Team without knowledge about the exercise which have to respond to the attacks by the RT. |
Context
During this blog I will not go into detail about what TIBER-EU or TIBER-ES is. I will simply mention that TIBER-EU is a European framework for testing red teaming with a threat intelligence approach. This approach is related to Lockheed Martin's well-known Intelligence Driven Defense® method.
The offensive tests will be from the perspective of actual attacks with procedures used by actors targeting the financial sector. For more information, I recommend reading the TIBER-EU and TIBER-ES guides.
info
TIBER-EU Information: https://www.ecb.europa.eu/paym/cyber-resilience/tiber-eu/html/index.en.html
TIBER-ES Information: https://www.bde.es/bde/es/secciones/servicios/tiber-es-3f6bfe7e907ed71.html
Goal of this project and blog
The main objective of this project is to help TI analysts during the testing phase (testing phase is the name given by TIBER). To do this, different cases are made available that can be imported into The Hive and thus be able to speed up the work.
For this, a total of 6 cases have been developed, which have sub-tasks assigned to different types of threat intelligence analysts (tactical, operational and strategic levels).
The phases of the red team and blue team will not be covered during this blog and neither in the cases of The Hive. In future posts I make, I will generate new cases for those teams.
Finally, in the phases and steps that come in this blog, it will not go into excessive detail about what needs to be done, since, in the cases that I have developed for The Hive, I put the necessary information for the threat intelligence analysts.
Process
The process that TIBER-EU makes available to the community is very interesting. The following image shows the activities carried out by the TI team within the testing phase.
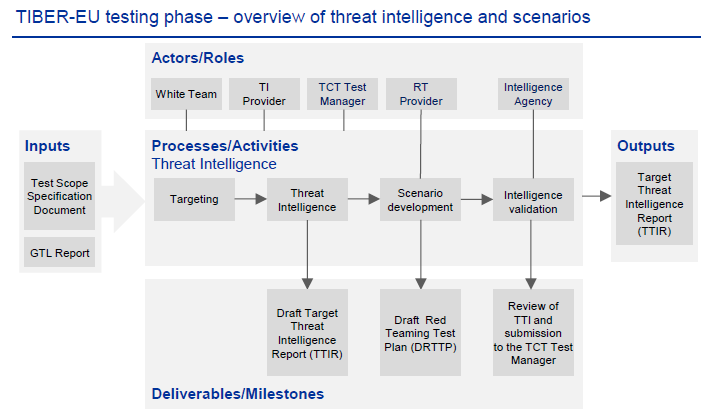
source: ecb.europa.eu
To simplify the entire TIBER-EU document and the Threat Intelligence section a bit, I wanted to make a process explaining the most important points of the framework for those analysts who are going to work on it. Specifically, I have focused on the "Processes/Activities Threat Intelligence" section of the official TIBER-EU process.
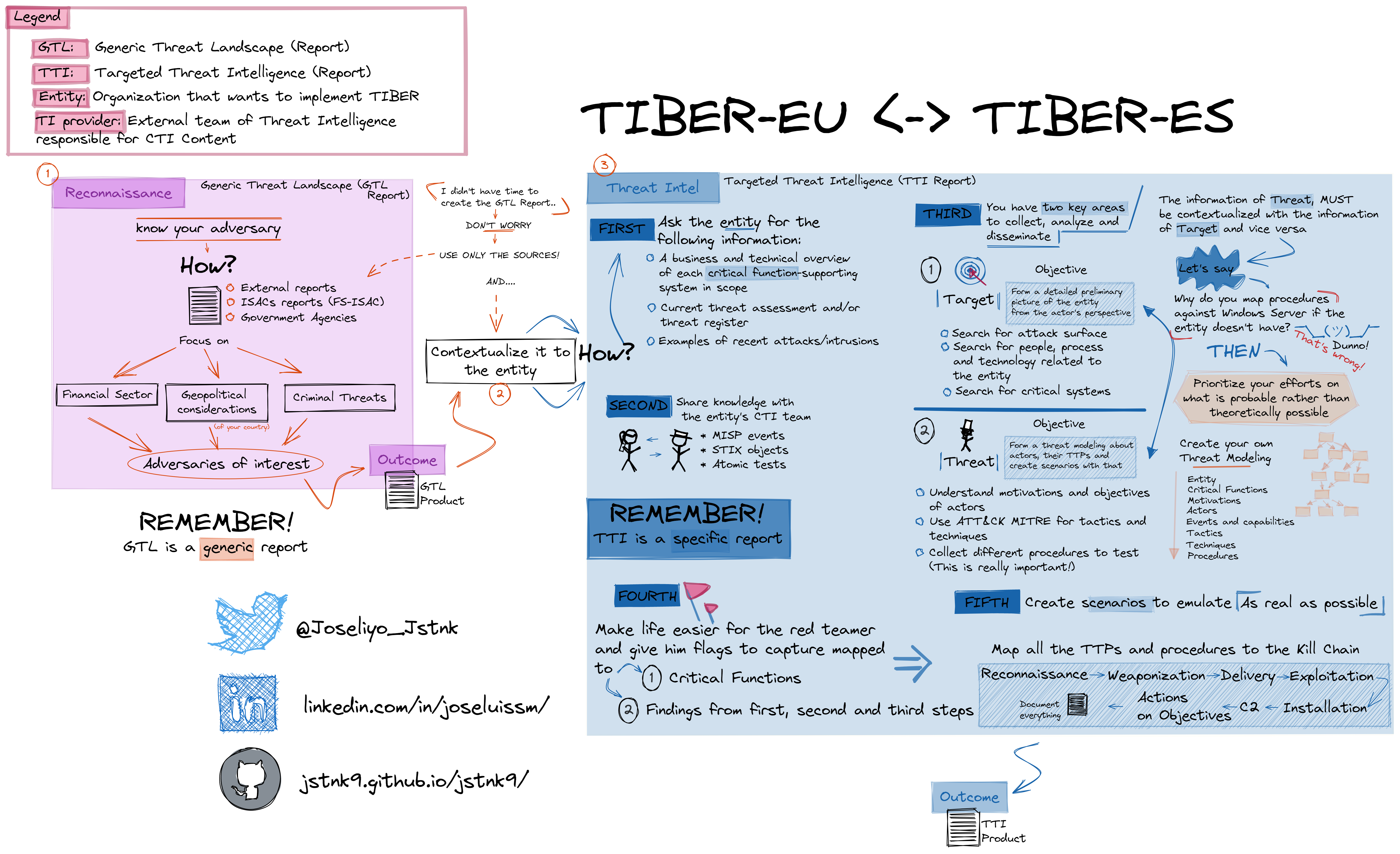
Generic Threat Landscape (GTL Report)


Before starting, it should be made clear that the objective of the GTL Report is, as its name indicates, to generate a generic report about the financial landscape.
That said, we must start by knowing our adversaries, for this, we will have to access different sources of information, if possible about threats from the financial sector. Some resources that we can use in order to know these financial threats may be the following.
- Reports developed by Cybersecurity Companies
- Reports developed by FS-ISAC
- Reports developed by Government Agencies
Depending on the country to which the Entity belongs and/or operates, we must focus on threats from the financial sector, with geopolitical considerations of the country and possible criminal groups that carry out operations against said sector (it is important not to focus only in APTs).
With this information, it is recommended to generate a generic report on the adversaries identified as potential.
In the event that resources or time are not available to carry out this report, it is advisable to use public reports on past intrusions against the financial sector. The GTL report is optional, it is not mandatory, however, TIBER-EU recommends doing it :-).
Targeted Threat Intelligence (TTI Report)


During the TTI phase, the clear objectives that the TI team has to achieve are summarized below.
- Contextualize the information from the GTL Report to the
Entity. This is achieved by identifying critical functions of theEntitywith its help - Share intelligence between the TI teams of the
Entityand the TI Provider - Focus the analysis efforts on two key points (Target and Threat) that will be described in the following points
- Create flags for the RT to get during his offensive tests. These flags must be contextualized with the information obtained from the
Entity - Create scenarios as real as possible about attacks that could occur in the
Entity. These scenarios must be mapped to the kill chain to make each objective in each phase clear to the RT. - Finally, a complete report will be generated with all the information. This report will be the entry point for the RT.
Step 1 - Context


The first step, as mentioned above, aims to contextualize the GTL report on the Entity. During this step, we will have to exchange information (as a list of assets, departments, services, etc.) with the Entity, this will help us to understand more how your business works and possible assets considered as critical.
If possible, it is also highly recommended to ask the entity for reports on recent intrusions that they may have suffered. That information may later lead to possible scenarios.
Ask yourself a question. How can you defend something if you don't know it? It is very important to know the Entity's business
Step 2 - Sharing Intelligence


The second step is entirely focused on sharing intelligence between the two TI teams. This sharing can be done through structured formats supported by technology (see STIX, MISP, etc...) as in PDF formats or any other on reports made by the TI team of the Entity.
Within this activity, it has more value if the Entity shares intelligence generated by itself than that which it has consumed from third parties.
Step 3 - Analysis


This is the most important step and in which you should invest more time. The analyzes should be separated into two key aspects.
Target: It is based on understanding the exposure of the
Entityfrom the point of view of an actor. Identify processes, people and potential technology to be targeted.Threat: We will have to map the motivations, objectives and TTPs of the adversaries with the interests of the
Entity. For this, a Threat Modeling will also have to be carried out to help us with this evaluation. The use of MITRE in this section is very important.
Make sure the information captured from Threat maps to Target. Just an example, imagine that the Entity hasn't Windows Servers, then...
Think about this.. Minimize your efforts
Why do you map procedures against Windows Server if the Entity doesn't have?
It doesn't make sense for you to simulate adversarial sharing scenarios against Windows Server if it's never going to have an impact on the Entity.
Step 4 - Flags


Setting flags for the RT to get is challenging. The flags must be realistic, from the point of view that an actor could also get said flag. All those flags must be contextualized with the Entity. They can range from targeting a specific person to open an email to exploiting an exposed service known to have vulnerabilities.
Step 5 - Create Scenarios


The last step is related to creating scenarios for the RT to execute and get those previously set flags. Think that these scenarios can be carried out by real opponents. It is important to spell out at a very low level what you want the RT to do.
The procedures must be described in full detail, for example, if you want the RT to execute a command with a specific parameter, it must be indicated like this.
Finally, all the scenarios that are developed must be mapped to the phases of the kill chain, which have a specific task in the case generated for this step.
The Hive
Import Case
Version of The Hive used:
Scalligraph: 0.1.0-SNAPSHOT
TheHive: 4.1.18-1
Play: 2.8.7
Before you begin, I highly recommend following the guide below to import the ATT&CK MITRE Matrix and MISP taxonomies into The Hive. To do this, go to the following links.
info
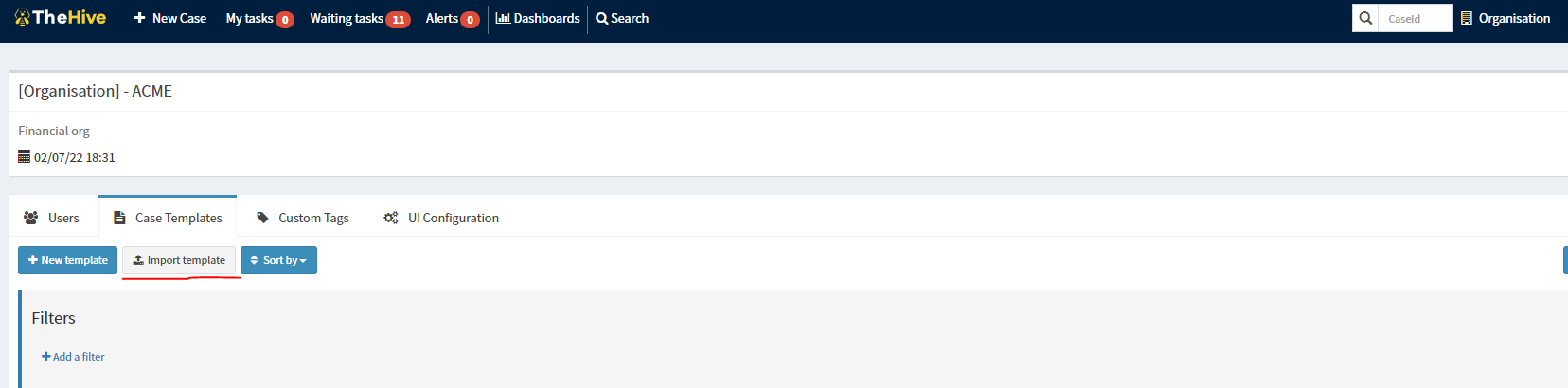
To import the cases, you must have permissions to perform this task. To do this, you must first navigate to the Organization section that is located at the top next to the search bar.

Once inside that section, we will have to go to the section that says Import template and select the JSON files that are in my GitHub, specifically in the cases folder.
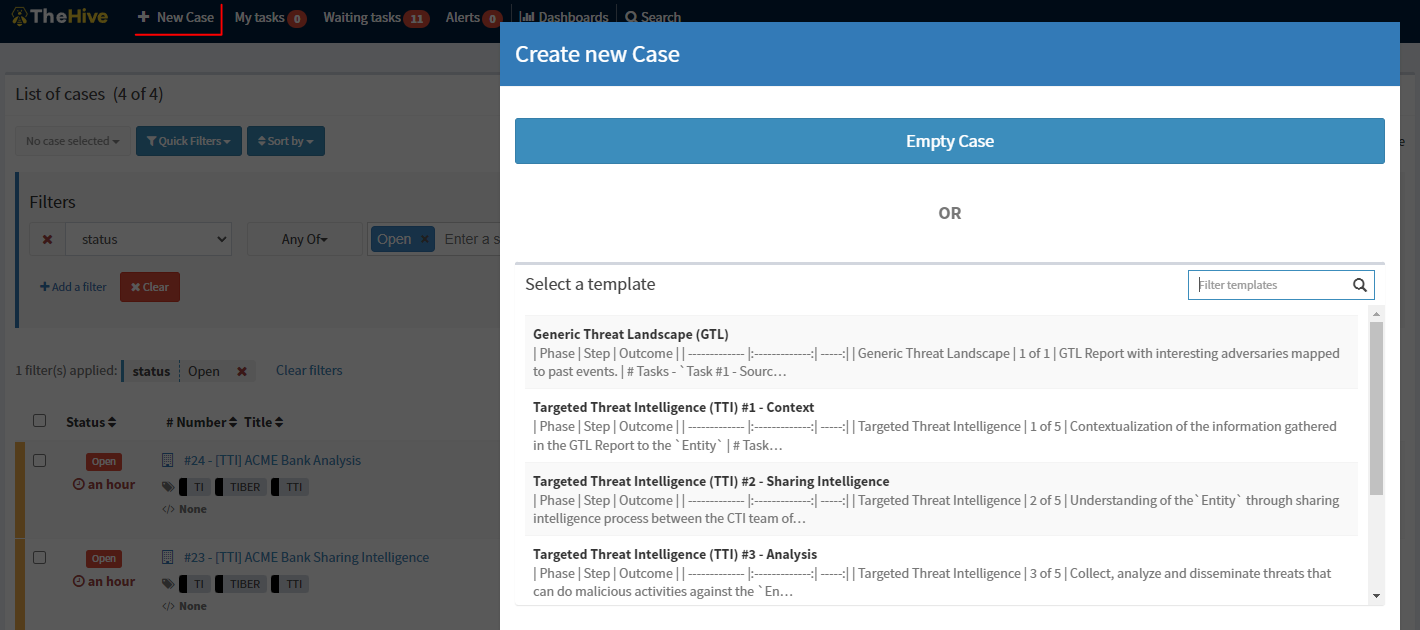
Once this is done, and when we click on the upper part where it says + New Case, all the imported cases will appear with the information about the TIBER-EU phases.
Case visualization
As an example, once the cases are imported and one is generated to start working on it, they look like the following image:
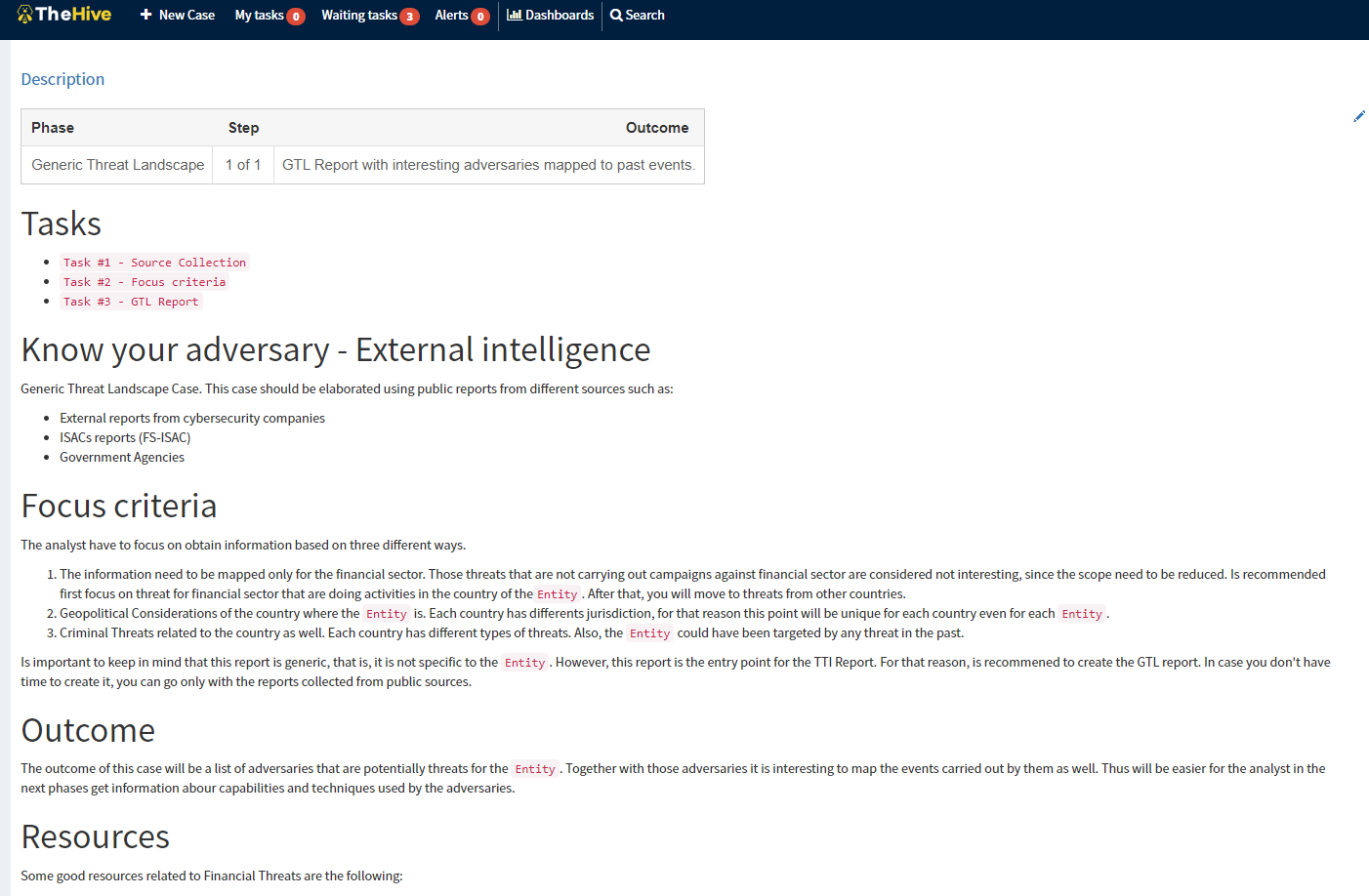
As can be seen, it contains all the information the analyst needs to start working. The way cases are written is by using markdown.
When clicking on tasks, the user can see the following information.
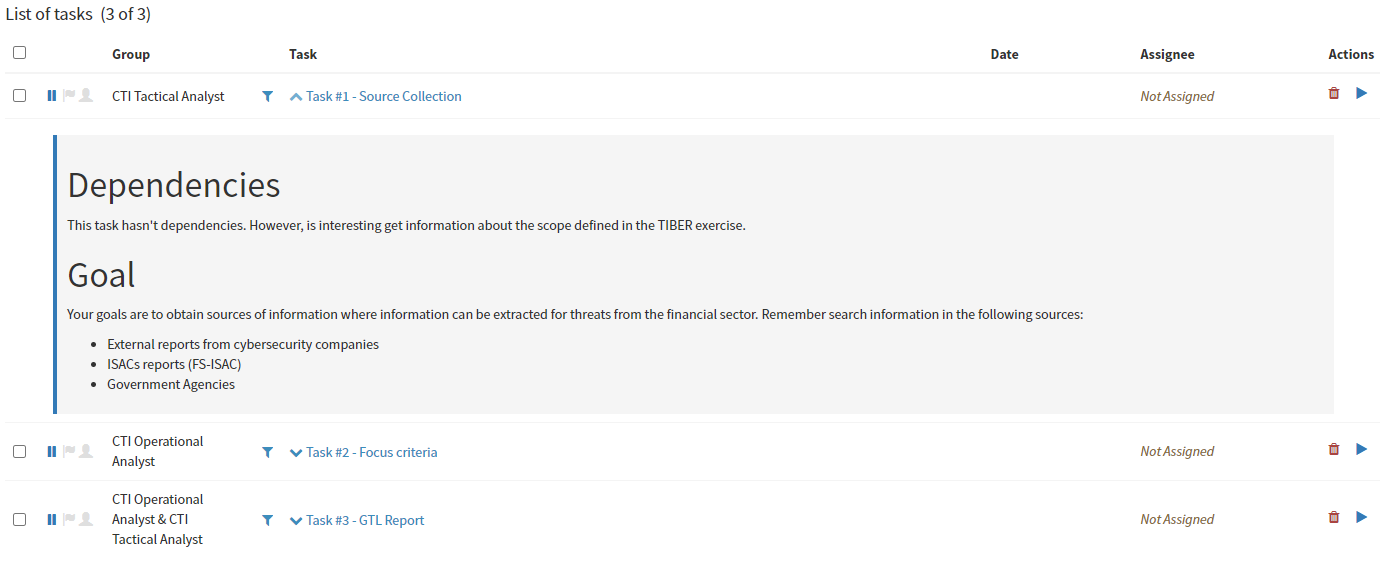
All the Tasks that are included in each case have dependencies and goals, this will help the analysts not lose focus and focus on the goals to be achieved.
Cases information
Here you can find basic information about the created cases. Case name is the name defined for each case. Each case has different tasks to complete. You'll find all the information in the json files.
- GTL
- TTI - Step 1
- TTI - Step 2
- TTI - Step 3
- TTI - Step 4
- TTI - Step 5
Case name: Generic Threat Landscape (GTL)
Tasks:
Case name: Targeted Threat Intelligence (TTI) #1 - Context
Tasks:
Case name: Targeted Threat Intelligence (TTI) #2 - Sharing Intelligence
Tasks:
Case name: Targeted Threat Intelligence (TTI) #3 - Analysis
Tasks:
Case name: Targeted Threat Intelligence (TTI) #5 - Scenarios
Tasks:
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
GitHub Project: https://github.com/jstnk9/TIBER-Cases
