TL;DR
I have created a new script to automate the ingestion of IOCs in MISP in object format. This script also automatically consumes information from VirusTotal to enrich the IOCs in case of exist in VT. However, the most interesting thing about this script is that it is able to automatically obtain the Sigma rules and MITRE techniques of the IOCs that we want to store in MISP, and add this information as Galaxies.
The stored galaxies are at the event level and at the object level, i.e. the event will have the total number of galaxies related to Sigma rules and MITRE techniques. Each object will have only the galaxies related to its behavior.
All you need to use the script is a VT API Key and to have the Sigma and MITRE galaxies in your instance. Since 2022-11-28 the Sigma galaxy is embedded in the default version of MISP. In case you don't have it, I recommend you to read this blog and use the script I made to create the sigma rules galaxy.
Object creator
Object creator is a python script that helps you to add IOCs (in object format) in your MISP with extra information and galaxies automatically. The information is retrieved from VirusTotal using the API Key. If the IOC is in VT, the information extracted is as follows:
- Files
- Sha256
- MD5
- Sha1
- ssdeep
- vhash
- tlsh
- mimetype
- filenames
- magic
- MITRE Techniques as MISP Galaxies
- Sigma rules as MISP Galaxies
- IPs
- IP
- ASN
- Country code
- network
- ASN Owner
- Domains
- Domain
- Registration date
- Resolutions
- URLs
- URL
- Host
- Port
- Resource Path
- Query string
- Event
- All the MITRE Techniques extracted from the files stored in the MISP event
- All the Sigma rules extracted from the files stored in the MISP event
Nowadays not all VirusTotal samples have MITRE and Sigma Rules techniques. In the case of Sigma Rules, it is sometimes difficult to obtain results, especially depending on the file type. In general, binaries usually get good results with the associated sigma rules, but some office documents do not always get the expected results.
It is important to mention that the Sigma rules that VirusTotal has at its disposal are essentially those from the public Sigma GitHub. They also have other sigma rules from vendors related to Sandboxing. How VirusTotal relates sample behaviors to Sigma rules is unknown.
Sigma rules from VirusTotal
To obtain the Sigma rules information from a file, the endpoint of files is queried. The returned object contains a key called sigma_analysis_results which stores information about the sigma rules that could be related.
Another associated value information is the log where the match could be obtained in the match_context key. Currently nothing is being done with that value in this script, however it is likely that some of the information it incorporates will be added in some objects :-).
The following object is an example obtained through the sample 1641c9494dd3eabd7131add274804d83a308eecb241a56931ce045412c32f0a26f in VirusTotal.
{
"rule_title": "Suspicious Schtasks From Env Var Folder",
"rule_source": "Sigma Integrated Rule Set (GitHub)",
"match_context": [
{
"values": {
"TerminalSessionId": "1",
"ProcessGuid": "{C784477D-A7ED-643C-F905-000000004400}",
"ProcessId": "3144",
"Product": "Microsoft\\xae Windows\\xae Operating System",
"Description": "Task Scheduler Configuration Tool",
"Company": "Microsoft Corporation",
"ParentProcessGuid": "{C784477D-A7EC-643C-F505-000000004400}",
"User": "DESKTOP-B0T93D6\\george",
"Hashes": "MD5=838D346D1D28F00783B7A6C6BD03A0DA,SHA256=8BE433049CCC271F04A8E625E9FB9BD3BCF15B4EDEB63497C00BD9CE1CD5C50E,IMPHASH=7EE4BC5589713B3470B8A950256E2E69",
"OriginalFileName": "schtasks.exe",
"ParentImage": "C:\\Windows\\System32\\cmd.exe",
"FileVersion": "10.0.17134.1 (WinBuild.160101.0800)",
"ParentProcessId": "4524",
"CurrentDirectory": "C:\\Users\\george\\Desktop\\",
"CommandLine": "schtasks /create /f /sc onlogon /rl highest /tn \"t-launcher\" /tr '\"C:\\Users\\george\\AppData\\Roaming\\t-launcher.exe\"' ",
"EventID": "1",
"LogonGuid": "C784477D-1D0C-6407-0BA7-030000000000",
"LogonId": "239371",
"Image": "C:\\Windows\\System32\\schtasks.exe",
"IntegrityLevel": "High",
"ParentCommandLine": "\"C:\\Windows\\System32\\cmd.exe\" /c schtasks /create /f /sc onlogon /rl highest /tn \"t-launcher\" /tr '\"C:\\Users\\george\\AppData\\Roaming\\t-launcher.exe\"' & exit",
"UtcTime": "1681696749",
"RuleName": "-"
}
}
],
"rule_level": "high",
"rule_id": "0533322c5c44794b71e761cd351a2459aad6e21ae95c9543d4c9fdb3c8fde6c4",
"rule_author": "Florian Roth (Nextron Systems)",
"rule_description": "Detects Schtask creations that point to a suspicious folder or an environment variable often used by malware"
}
As you can see, among the information obtained is the id of the rule, author, title and other information. In this case, the necessary information would be the name of the rule, which is the same that will be previously stored in the Sigma galaxy.
INFORMATION
In case the sigma rule identified in the sample through VirusTotal is not found in the public Sigma GitHub, such rule will be added as a Tag and not as a Galaxy, since it will not be previously stored.
The sigma rules will be added in two different ways. The first one is globally in the event. For example, if we want to add 5 IOCs in a MISP event and the total of sigma rules identified in those 5 samples are 17 rules, 17 new galaxies will be created in the MISP event. On the other hand, for each of the 5 IOCs an object is generated as an attribute, and each object will have related sigma rules that have been seen in its behavior. In this way, the event and each object are characterized globally.
MITRE Techniques from VirusTotal
The same way that the sigma rules are obtained is done with the MITRE techniques. In this case the endpoint is different, since information is consumed from the behavior, being behaviour_mitre_trees.
Currently the information from the Zenbox sandbox is consumed, but it is planned to add the value of other sandboxes. The reason for choosing Zenbox is because it is usually the sandbox that obtains more results from the analyzed samples.
An example of a response obtained from VirusTotal could be as follows.
"mitre_attack_techniques": [
{
"signature_description": "Creates files inside the user directory",
"id": "T1036",
"severity": "IMPACT_SEVERITY_INFO"
},
{
"signature_description": "Sample is packed with UPX",
"id": "T1027.002",
"severity": "IMPACT_SEVERITY_INFO"
},
{
"signature_description": "PE file has section (not .text) which is very likely to contain packed code (zlib compression ratio < 0.011)",
"id": "T1027.002",
"severity": "IMPACT_SEVERITY_INFO"
}
]
Event Creation
At a high level, the process to create a new event in MISP based on the IOCs you want to store is as follows.
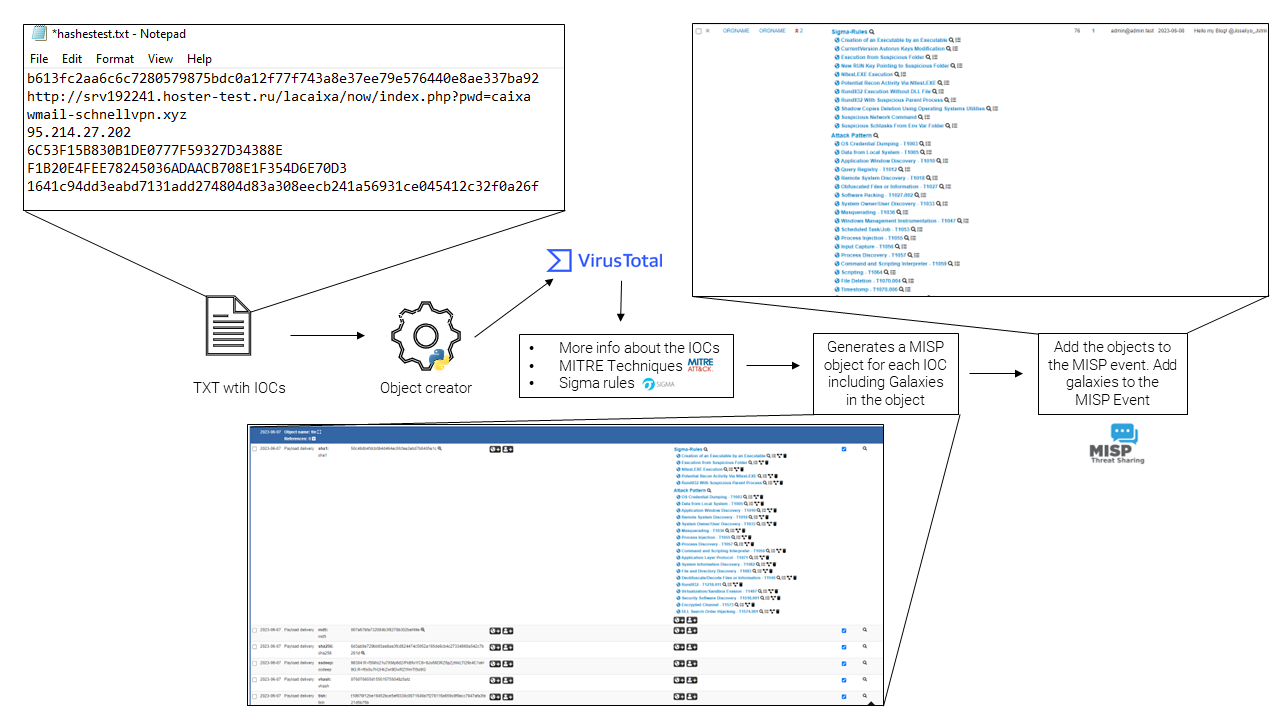
As stated above, galaxies are stored both in the objects and in the event itself. This will allow us to identify the exact sigma rules and techniques used by a specific sample.
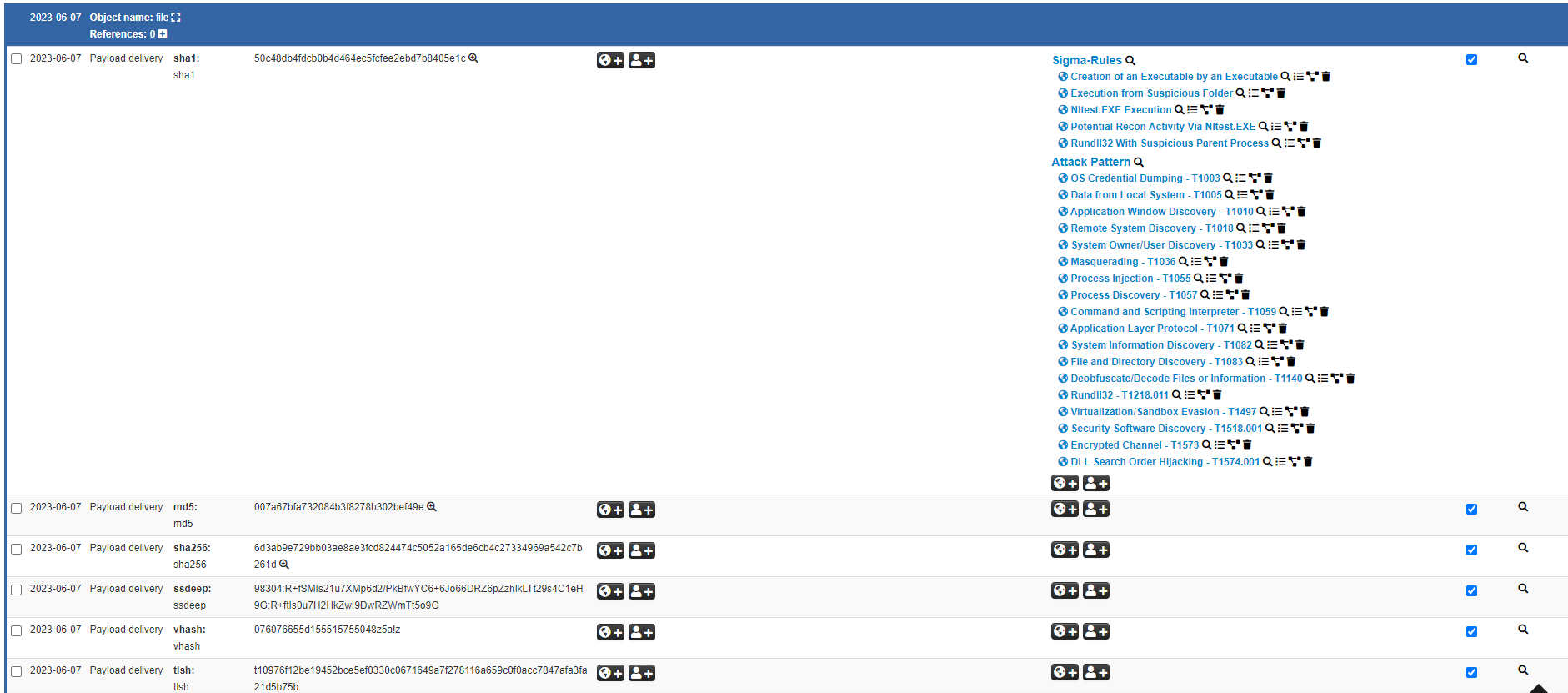
An example of an object created with the information extracted from VirusTotal to enrich it and with the corresponding galaxies would be the following.
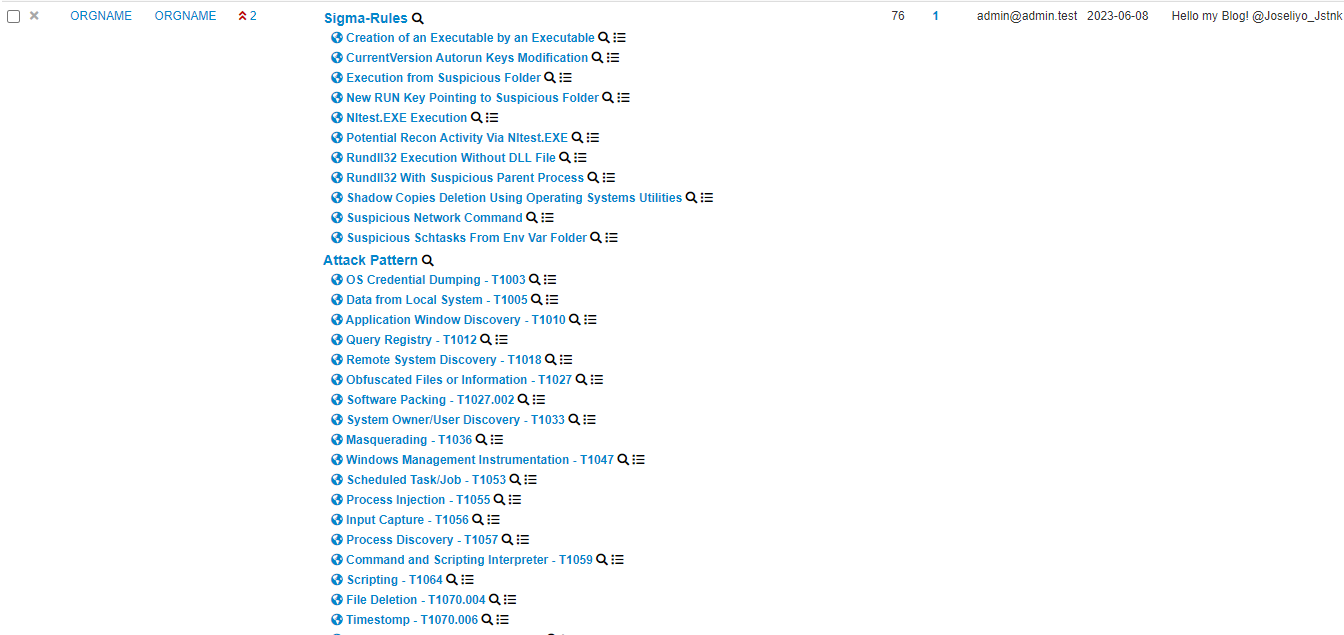
As for the event, as explained it will contain all the galaxies of all the objects. An example of an event created from the ingestion of 7 IOCs is the following.
GitHub Repo
If you want to use this script and get more information about how to use it, please go to the public GitHub repo.
I have in mind to improve this script. During the next months I will be updating the GitHub repo.
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
GitHub Project: https://github.com/jstnk9/MISP/tree/main/object-creator
