Summary
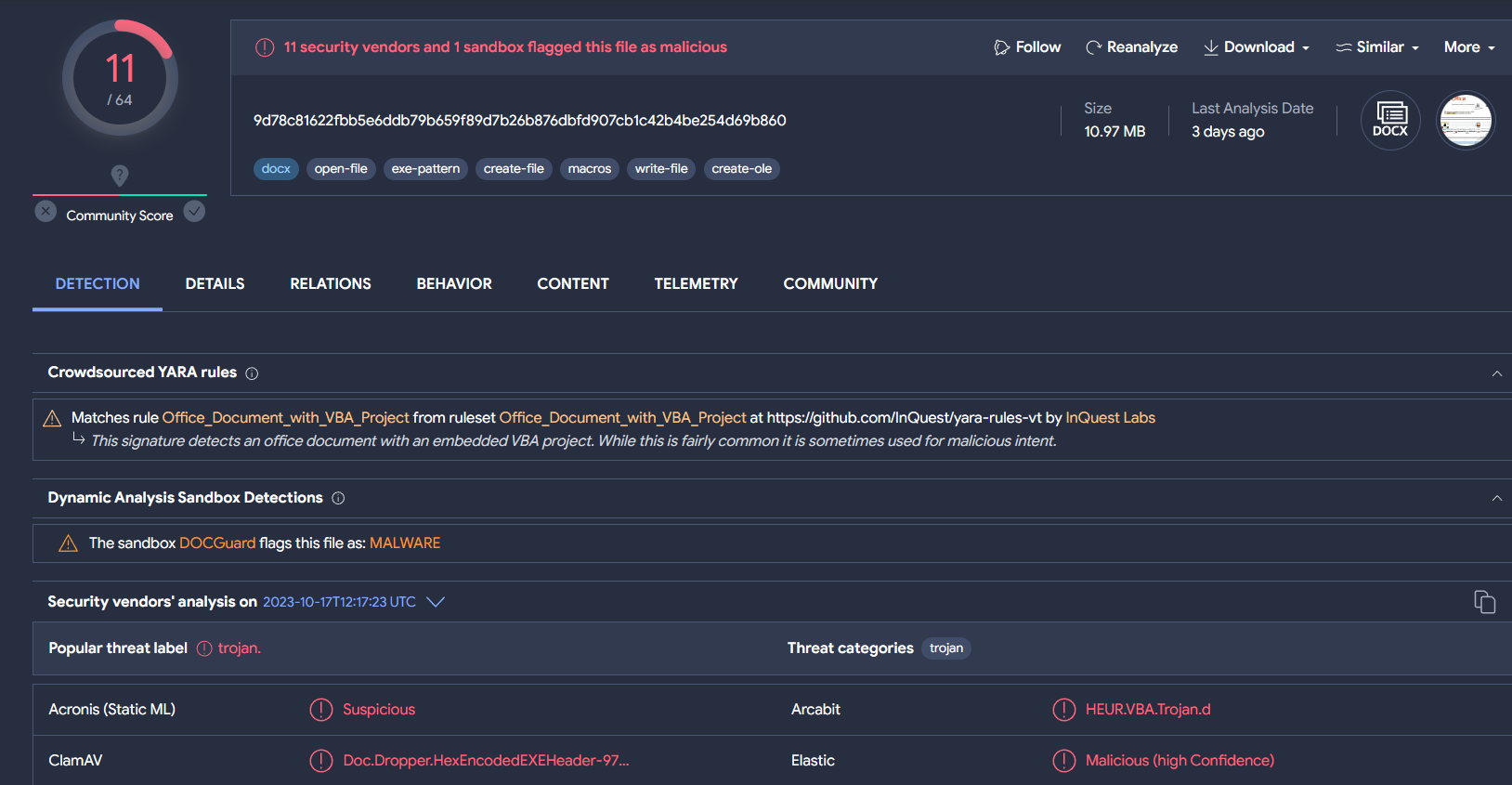
On October 16, a malicious file that could be related to the current Israel-Gaza conflict was uploaded to VT. The document is related to Joe Truzman publication "IRAN AND ITS NETWORK OF NINETEEN TERRORIST ORGANIZATIONS ON ISRAEL'S BORDERS" on fdd.org and talks about terrorist organizations that receive funding, training, and weapons from Iran's Islamic Revolutionary Guard Corps.
The actor behind this document could not be determined, however, due to the type of document and the characteristics analyzed, it could be an APT. As for the victims, it could be Israel institutions.
warning
Information about the origin and destination of the document could not be confirmed. What has been described in relation to suspected sponsors and victims is just conjecture.