ICYMI
Before reading this blog I recommend you to read the first part of it: https://jstnk9.github.io/jstnk9/blog/Sigma-Rules-as-MISP-galaxies
MISP has already added this galaxy to its repository.
Cluster: https://github.com/MISP/misp-galaxy/blob/main/clusters/sigma-rules.json
Galaxy: https://github.com/MISP/misp-galaxy/blob/main/galaxies/sigma-rules.json
Version 2.0
During the last weeks, I have been working on the script to improve it and to allow in this new version that I have recently published, the possibility to add relations in the galaxy with another already existing MITRE ATT&CK. This, among other things allows to know in a quick and visual way which sigma rule is related to which technique within MISP.
Suppose you have an event in MISP that is mapped to 5 MITRE ATT&CK techniques. Now, by clicking on those techniques and expanding the relationships, you will be able to see if there is any sigma rule that can cover any behavior of the expanded technique.
ATT&CK MITRE Galaxy
If you have MISP deployed, you probably use the MITRE ATT&CK galaxy. That galaxy is found by default when you install MISP, as is the Sigma galaxy now. You can find it here mitre-attack-pattern.json.
If we access to any cluster of our galaxy, there is a button where it says Toggle Cluster relationships, clicking on it, we can see the relationships that this cluster has.
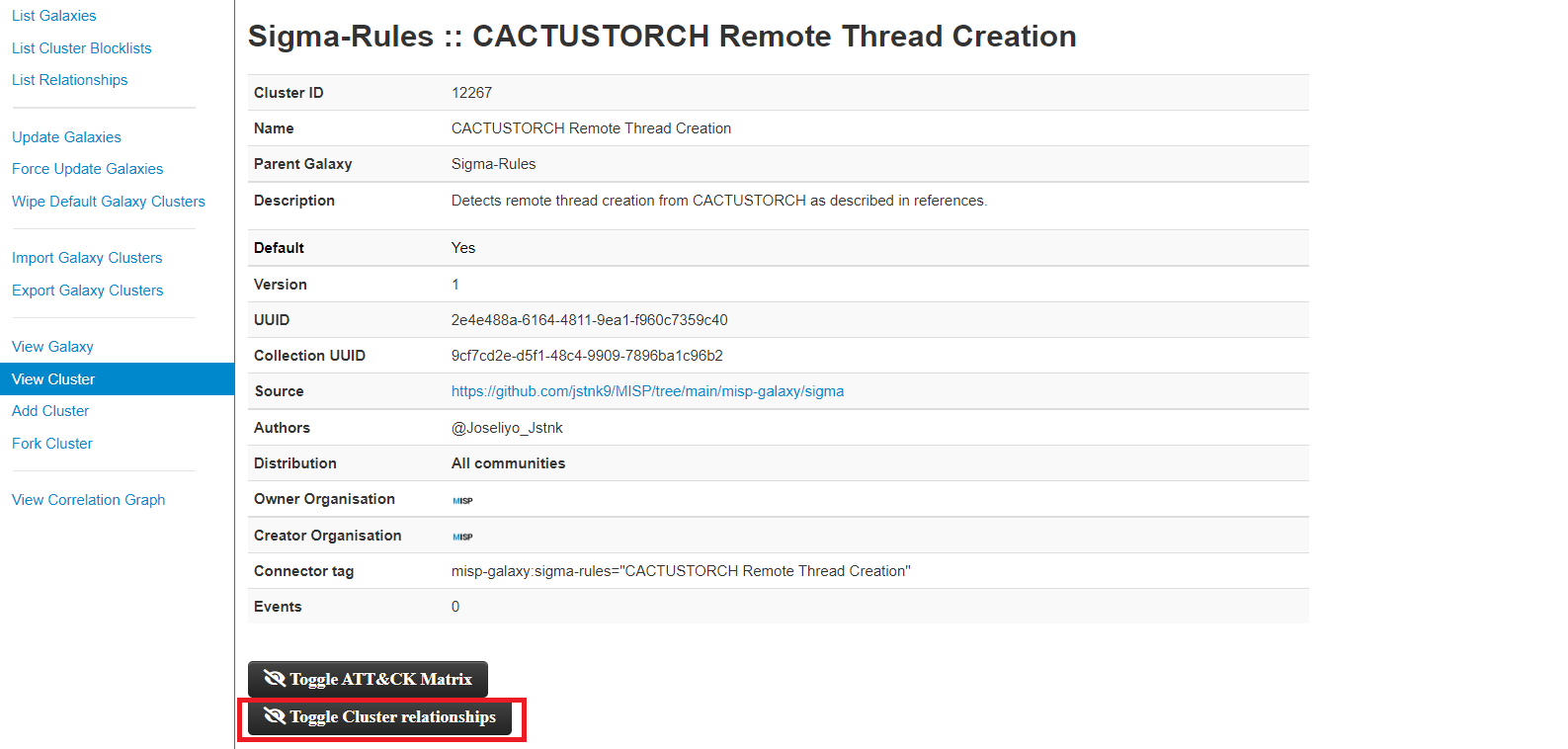
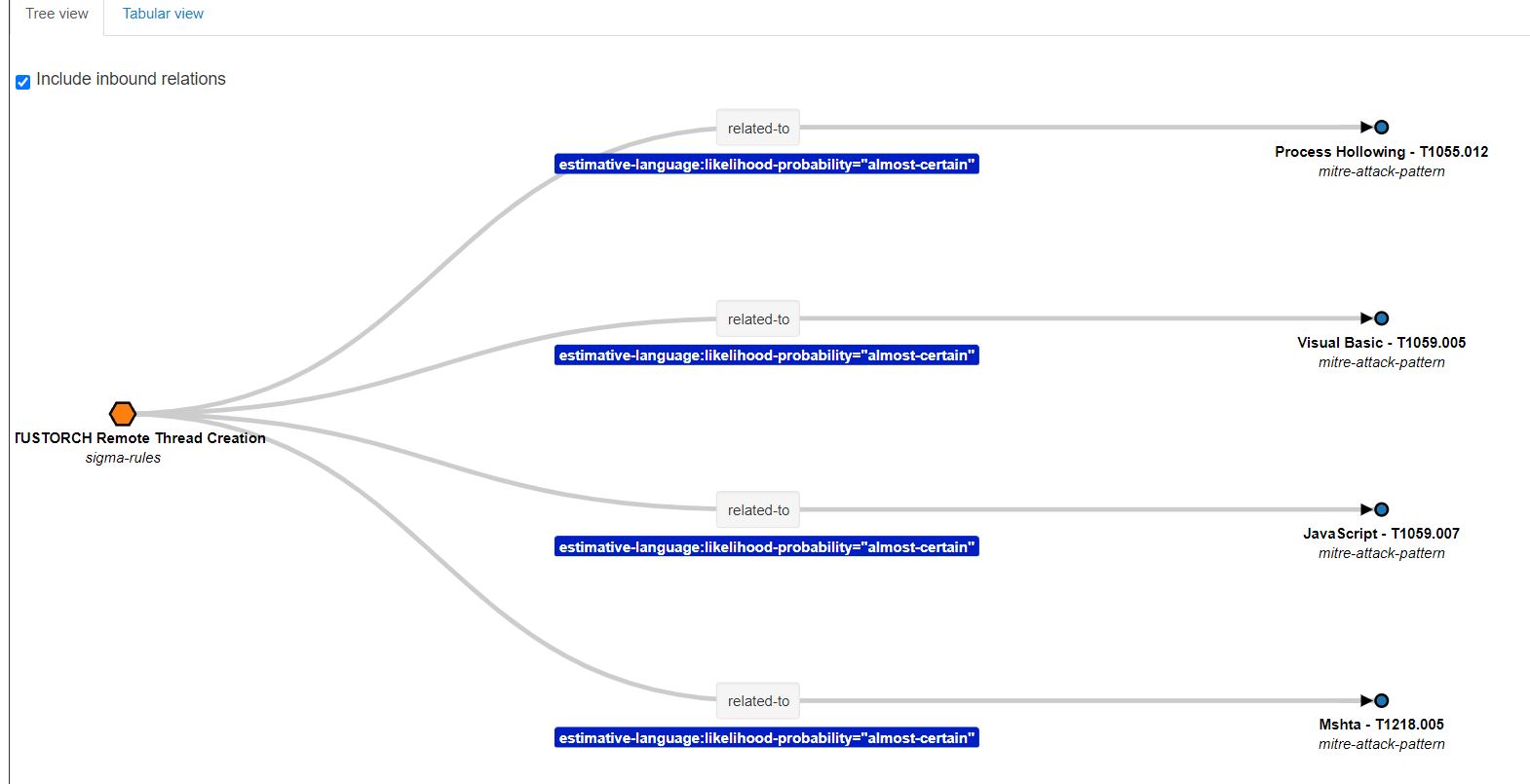
Subsequently, the drop-down list will open with the relationships that the sigma rule has with the MITRE techniques, in case there is any relationship.
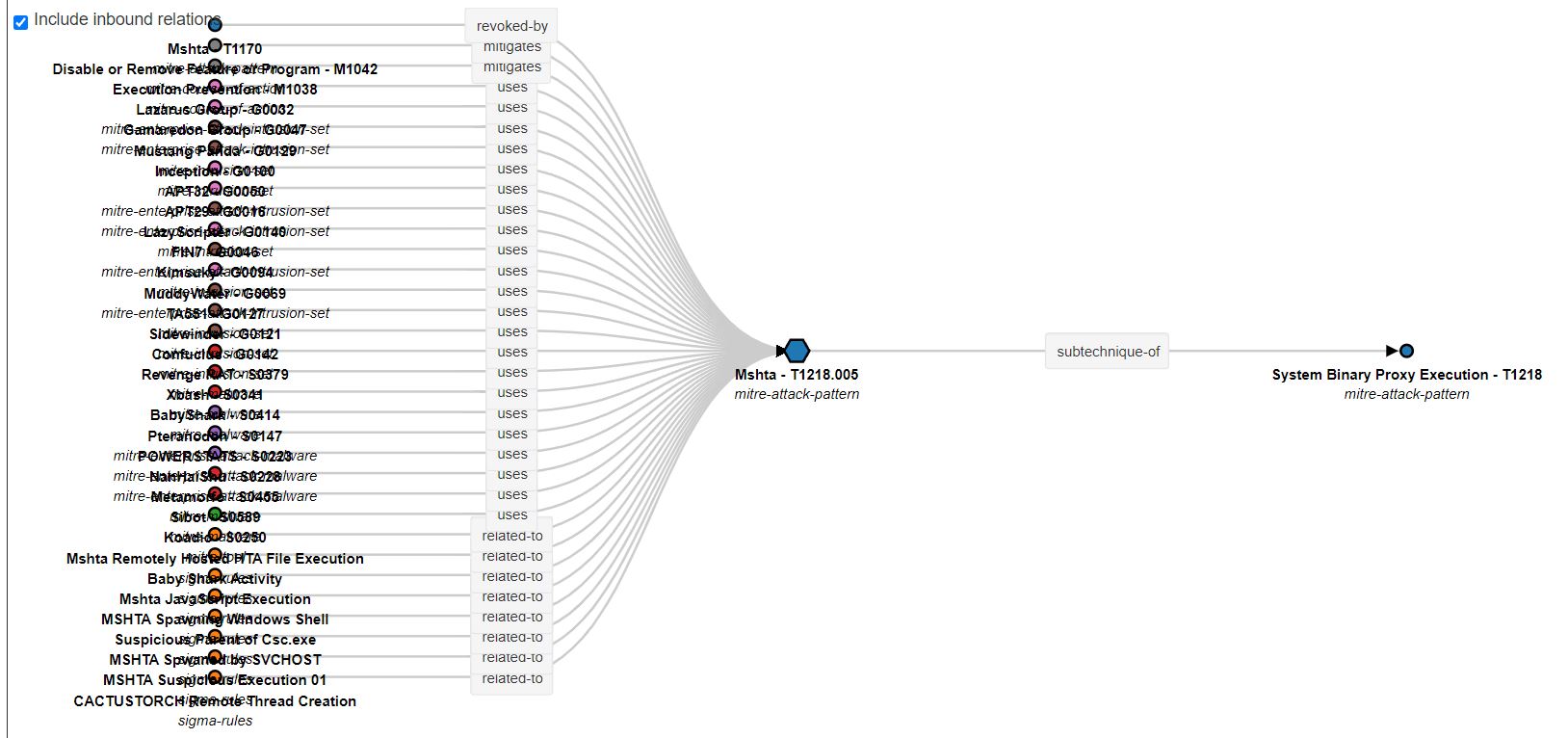
On the contrary, if we access the cluster of a MITRE ATT&CK technique, we can see all the relationships it has, such as tools, MITRE mitigations and also, our sigma rules.
Generate the galaxy
To generate the galaxy is very simple. The first thing to do is to clone the repository and install the requirements from the file requirements.txt. It is important to mention that python3 is required to run the script.
pip3 install -r requirements
Once installed, something new in this 2.0 version is the file config.ini. The inclusion of this file is necessary so that the user who is going to execute the script, indicates the path where the galaxy related to MITRE ATT&CK is located. Generally, the directory will be the one indicated in this file, however, if the installation was done outside /var/www/MISP, it is important that you modify it.
[MISP]
cluster_path = /var/www/MISP/app/files/misp-galaxy/clusters/
mitre_attack_cluster = mitre-attack-pattern.json
The content of the cluster_path variable contains the path where the MISP clusters are located. On the other hand, the content of the variable mitre_attack_cluster is the ATT&CK MITRE cluster with the MITRE techniques and tactics.
Once we make sure that the configuration file contains the correct information, we will need to have cloned the Sigma Rules repository. If instead of using the Sigma Rules repository we want to use our own sigma rules, we can also do this (just change the path in the -p parameter). In this case, we will use the original repository and run the following command to generate the galaxy and the cluster.
python3 sigma-to-galaxy.py -r -p /opt/sigma/rules
The -p parameter is used to indicate the path where our sigma rules are located. The -r parameter indicates that it is executed recursively, that is, if within the /opt/sigma/rules directory there are subfolders with more rules, these will be incorporated.
Finished, we will obtain the two files of the galaxies and clusters that we will have to put in their corresponding folder, as it was indicated in the first blog.
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
GitHub Project: https://github.com/jstnk9/MISP
Mastodon: @Joseliyo_Jstnk@infosec.exchange
References
- https://www.misp-project.org/misp-training/a.10-galaxy-2.0.pdf
- https://twitter.com/adulau/status/1611386536225902596
- https://github.com/SigmaHQ/sigma
- https://github.com/MISP/misp-galaxy
- https://github.com/jstnk9/MISP/tree/main/misp-galaxy/sigma
- https://www.misp-project.org/galaxy.html
- https://jstnk9.github.io/jstnk9/blog/Sigma-Rules-as-MISP-galaxies
