Information
I was doing some hunting looking for documents uploaded from Azerbaijan and Armenia due to the conflict that currently exists in both countries.
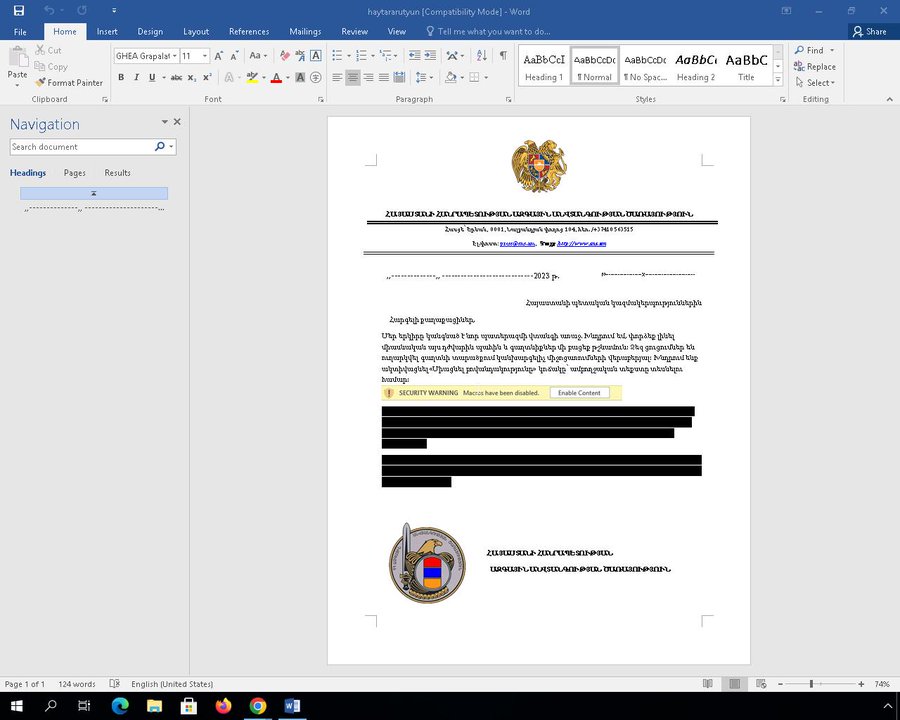
Then I found a suspicious document impersonating the National Security Service of the Republic of Armenia.
| Field | Value |
|---|---|
| sha256 | fa406c532ea3d7cae05411df0ed5a541630a07f26a247a22d907f424397c72ce |
| filename | haytararutyun.doc |
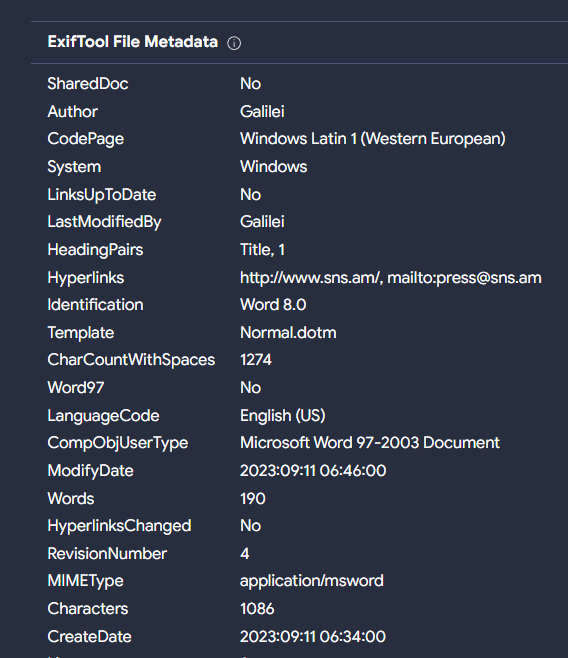
Taking a look at the relations in that file, there is an email parent. In the information of the email looks like it was sent to an account of sns[.]am, domain related to the National Security Service mentioned above.
Besides that, the metadata information related to the office document, shows information of the victims as well.
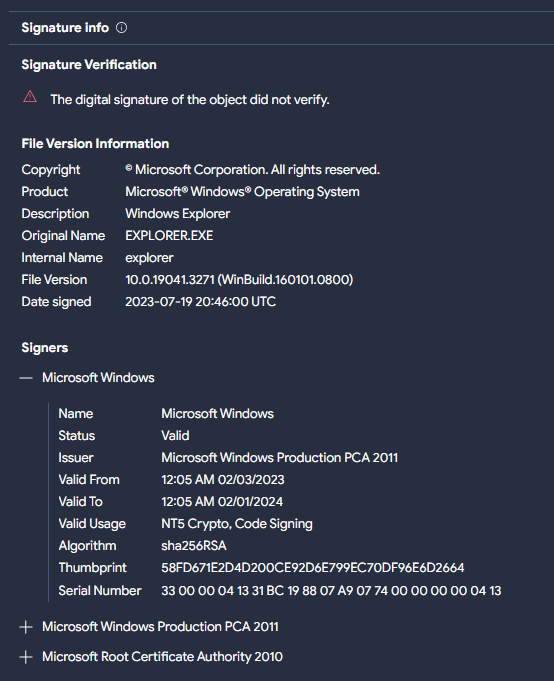
When executed, it downloads a file from https://karabakhtelekom[.]com/api/ekeng-mta.exe which tries to masquerade as explorer.exe using the same name
🔗 office document: https://www.virustotal.com/gui/file/fa406c532ea3d7cae05411df0ed5a541630a07f26a247a22d907f424397c72ce
🔗 Explorer.exe downloaded: https://www.virustotal.com/gui/file/3a679cb98f88d7d6bd84dcfe9717238c08c05942055bdb798103224e7f2f2ca9
🔗 tweet: https://twitter.com/Joseliyo_Jstnk/status/1704516647468388552
Hunting
The initial VT intelligence query used was the next one, due to the conflict I was looking for documents uploaded from those countries mainly.
(submitter:AM or submitter:AZ) type:document p:1+ fs:2023-09-01+
You can adapt this query to your needs. It was useful in a specific moment, but maybe is not interesting create a livehunt or use it daily for the false positives that will generate.
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/